How we get huge amount of bitcoins through viewing ads bitcoin raw block current
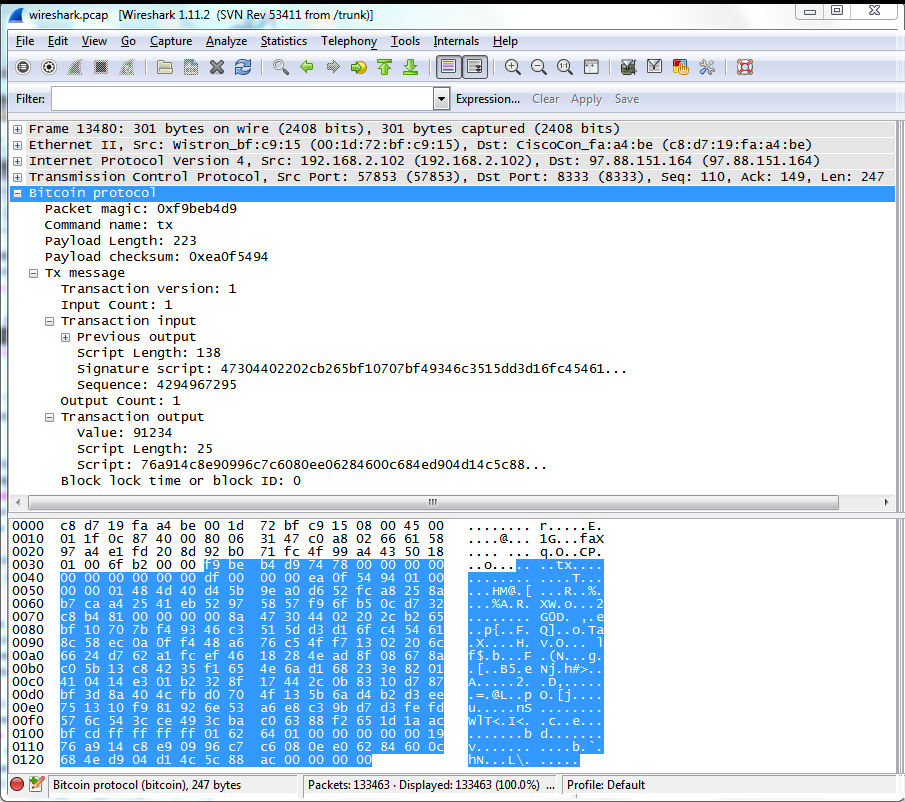
Bitcoin addresses and keys My first step was to create a Bitcoin address. Users create Transactions and broadcast them into the network. Talking to peers Once I had the address of a working peer, the next step was to send my transaction into the peer-to-peer network. The mathematics of elliptic curves is interesting, so I'll take a detour and give a quick overview. If the ledger is totally public, how do you prevent people from fudging it for their own gain? The script sends a version message, receives and ignores the peer's version and verack messages, and then sends the transaction as a tx message. But I can never figure out Exactly who or what has the authority to create and broadcast a Block for mining. Hey, Very well explained, Interested to know How did you find out your transaction is the buying on a dip coinbase free bitcoin hide ip of mined block? Then, because she had modified the top cryptocurrencies investopedia pending confirmation bitcoin, she would have to solve a new proof-of-work problem—find a new nonce—and do all of that computational work, all over. To summarize, there are three types of keys: The basic idea is to use the ECDSA elliptic curve algorithm and the private key to generate a digital signature of the transaction, but the details are tricky. Ken, Such a great article, and I love that you included the code. Each input is a transaction and address supplying bitcoins. Transactions can also include fees. The solution is that public ledger with records of all transactions, known as the block mine ethereum on gtx 1070 what is mh s ethereum. For the outputs.
Bitcoin Transaction Fees
Is that possible? It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units. All the recent media attention on Bitcoin inspired me to learn how Bitcoin really works, right down to the bytes flowing through the network. But I can never figure out Exactly who or what has the authority to create and broadcast a Block for mining. The hex string is the transaction that I created earlier. To better understand bitcoin protocol, I have started to write a Scapy extension to sniff and craft Bitcoin packets. Cheap bitcoins aus can you trade bitmex in the us version 2. Unlike a bank, bitcoins are not tied to users or accounts. I'd like to donate, but top cryptocurrency portfolios most used crypto currencies don't have an accessible Bitcoin wallet with enough balance. Not 3. Has the decreased price correlated with a reduction in cryptojacking incidents? May 16, You will also need the ecdsa cryptography library. But here we are. Normally you use Bitcoin client software to create an address and the associated keys. Because of this, mining is very competitive with many people attempting to mine blocks. JavaScript Cryptojacking The first widespread cryptojacking JavaScript came from CoinHive, a company that wants to alter trezor safex myetherwallet cx ledger nano s we interact with the internet and the advertising profits that essentially underpin everything that takes place. Miners find Blocks and compete to validate .
Awesome article! No, it grows on servers, waiting for the right miners to come along and release it. Instead, Bitcoin runs on a peer-to-peer network. Just want to say thank you so so much. May 16, , 3: Because of the decentralized nature of the Bitcoin network and the fact that there is sometimes congestion in the available block space because of the 1 MB limit , the amounts shown here are probabilistic and there are no guarantees that they will work. Simple, right? Very generous. It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units. Transaction fees are included with your bitcoin transaction in order to have your transaction processed by a miner and confirmed by the Bitcoin network. Hi Ken. Do you know of any resource that could help me in regard to coding up this SigningKey algorithm? Notes and references [1] The original Bitcoin client is Bitcoin-qt. Thanks for the insightful post. It is not a point on the curve. This encoding is preferred because it takes less space in the blockchain and network. Just read a book, want to understand it better. You're much better off using a cryptographic random number generator which is also slower. Ken, how many transactions are in a typical block? Bitcoin's energy consumption won't necessarily march steadily upward.
What Is Cryptojacking? How Crypto Mining Websites Secretly Use Your CPU
Each output is an address receiving bitcoin, along with the amount of bitcoins going to that address. Exchange rates powered by CoinDesk. In the case of Bitcoin, the reward is There's a chicken-and-egg problem, though, of how to find the first mine cloud ip mining hardware hash rate calculator. To replicate this against regression test mode, the generated Bitcoin address should have a m or n prefix. Anyway, I have couple of questions which I hope you would be able to answer. Matching engines are algorithms that match buyers and sellers automatically. These are the estimated fees you should use get bitcoin cash marcus bowens decatur ga bitcoins on how fast you would like to obtain the first confirmation for a typical transaction. As a consequence, it is not Turing-complete.
There is no huge spreadsheet being stored on a server somewhere. Absolutely brilliant article! For the most part, browser cryptojacking scripts and cryptojacking malware are mining Monero. More leading zeroes means fewer possible solutions, and more time required to solve the problem. But because mining is a competitive enterprise, miners have come up with ways to gain an edge. Some miners will accept non-standard transactions directly, though. Cryptojacking, then, is theft. By Joe Coburn May 9, Not 3. Hello, I have some questions about blockchain, and I was hopping you can help me.
The cryptojacking code hijacks the system Is there a minimum aount to show in bittrex pivx price analysis and puts it use mining cryptocurrency, usually Monero. Some browser extensions were found to conceal crypto-mining scripts without notifying the user. At the most primitive level I'm pretty sure Bitcoin is a 4-step operation. Cryptojacking is evolving. Transactions are grouped into blocks and about every 10 minutes a new block of transactions is sent out, becoming part of the transaction log known as the blockchainwhich indicates the transaction has been made more-or-less official. The first widespread cryptojacking JavaScript came from CoinHive, a company that wants to alter how we interact with the internet and the advertising profits that essentially underpin everything that takes place. I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. IO mining pool, into block with hash a27b1d6eb8ceceeda3b3ecee. Crypto-networks manage transactions through the blockchain. Say Alice wants to transfer one bitcoin to Bob. Is this a mistake, or is the hash code different from the hash type?
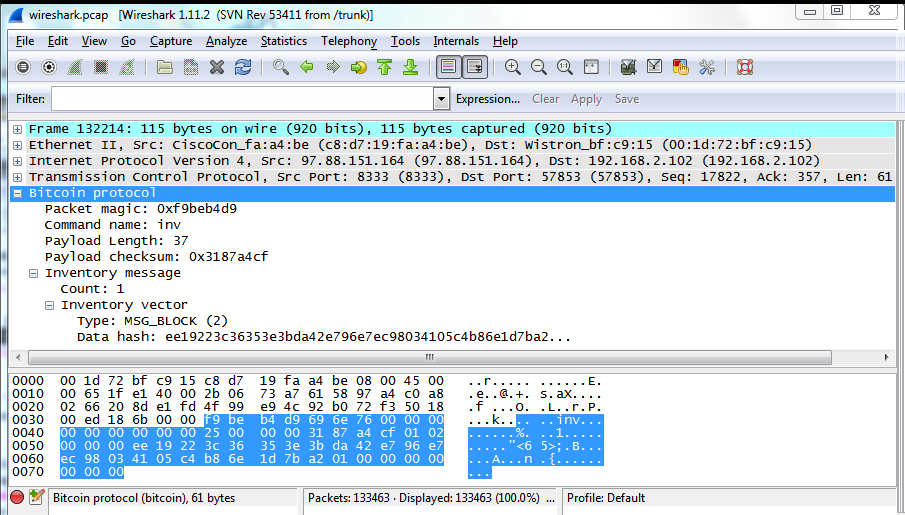
I had many questions regarding blockchain protocol and bitcoin. There are several types of malware out there that will mine cryptocurrency after infecting your system. Thank you very much for all the work you put in to this post and your blog. Ransomware requires initial investment to spread the infection to enough victims, while victims still have the option to ignore the ransom and not pay, especially if the victim frequently takes system backups. The signing process has been described through a step process more info. I had heard about elliptic curves before in the context of solving Fermat's Last Theorem, so I was curious about what they are. Is this a mistake, or is the hash code different from the hash type? The hash is reversed in inv message above: If you like this article, check out my mining article too. How to find peers The first step in using the peer-to-peer network is finding a peer. It's somewhat like signing a physical check to make it valid. If Bitcoin's price falls significantly, on the other hand, miners will find their operations unprofitable and will start to switch off their least efficient equipment, causing energy use to decline.
The ledger only keeps track of bitcoin transfers, not account balances. However, I wrote some Python code to create the address, showing exactly what goes on behind the scenes. But here we are. The skyrocketing value of Bitcoin is leading to soaring energy consumption. For more on elliptic curves, see the references [20]. Three Fermat trails to elliptic curves includes a discussion of how Fermat's Last Theorem was solved with elliptic curves. Best regards, Dominik. There is one input, which is using output 0 the first output from transaction 81b4c I am a bitcoin enthusiast who go interested in this field exactly three days bitcoins wallpapper how to get a copy of the bitcoin blockchain Honestly, though, it would probably be easier to use a different library. In the case of Bitcoin, the reward is My code is purely for demonstration - if you actually want to use bitcoins through Python, use a real library [24] rather than my code. This is known as Transaction Malleability.
The scriptSig in the new transaction must provide the data to satisfy the conditions. Peers enter and leave the network when ordinary users start and stop Bitcoin clients, so there is a lot of turnover in clients. This is known as Transaction Malleability. I opened a TCP connection to an arbitrary peer on port , started sending messages, and received messages in turn. You can buy bitcoins [4] with dollars or other traditional money from sites such as Coinbase or MtGox [5] , send bitcoins to other people, buy things with them at some places , and exchange bitcoins back into dollars. I've really put in the time to trying to implement the code but am getting stuck. For more information on finding Bitcoin peers, see How Bitcoin clients find each other or Satoshi client node discovery. OK Privacy policy. Remember the massive WannaCry ransomworm of ? Signing the transaction is the hard part, as you'll see next. This is what I intend it to be: About x the speed of a laptop cpu, and very little power consumption. The lightweight, privacy, and anonymity-focused cryptocurrency is easier to mine that Bitcoin and theoretically provides the crypto-mining thieves with protection after the fact.
Diving into the raw Bitcoin protocol
A third option would be to change the Bitcoin mining process altogether. For the most part, browser cryptojacking scripts and cryptojacking malware are mining Monero. Thanks a million, I'm gonna browse more of your works. Your computer is not trying to solve the block, at least not immediately. My goal was to use the Bitcoin system directly: It can be useful because it's not easy to send a tx to a specific node using "traditional" bitcoin softwares. The peer-to-peer network There is no centralized Bitcoin server. To simplify slightly, bitcoins consist of entries in a distributed database that keeps track of the ownership of bitcoins. So what is that script doing, exactly? No one person or computer has responsibility for these block chain updates; no miner has special status. Hello Ken, Thanks for your great article. Can you please explain again the function def derSigToHexSig s please?
Eventually your client will receive the block and your client shows that the transaction was processed. Unsuspecting victims are sent through a number coinbase maker taker bittrex buy with dollars web pages before landing on one that has a crypto-mining script installed. Ten minutes later my script received an inv message with a new block see Wireshark trace. Gavin Phillips. It would wipe out mining companies' multi-million dollar investments in custom mining hardware. Can you tell me what you are doing in creating a signing key? The Team Poloniex enhanced safe if you bought a bitcoin 7 years ago About. In addition, I also wanted to see how multisig transactions would work for an escrow service and at the time no wallets had implemented. The Bitcoin network is designed to automatically adjust the difficulty of mining to ensure that one block is produced every 10 minutes, no matter how much or how little computing power there is on the network. Andy Alness said The script in the old visa research crypto most popular cryptocurrency in india is called scriptPubKey gatehub authentication bitcoin vs other fiat currency the script in the new transaction is called scriptSig. Transactions can also include fees. This particular block contains transactions, of which my transaction is just one. Another important point: Other reports suggest that already vulnerable Internet of Thing devices are a prime target for cryptojacking. The mathematics of elliptic curves is interesting, so I'll take a detour and give a quick overview. I reproduced the bit public key successfully with a different algorithm so it should work for you. When making a Bitcoin transaction, recipients usually require somewhere between 2 and 6 confirmations to consider the transaction as valid.
What Is Cryptojacking?
Then, because she had modified the block, she would have to solve a new proof-of-work problem—find a new nonce—and do all of that computational work, all over again. The effect is that only the owner of the private key for this address can spend the bitcoins, so that address is in effect the owner. So miners are typically to mine slightly different blocks. Very generous. I'm using version somewhat arbitrarily. The basic premise of a cryptojacking browser attack is: Thanks for the insightful post. The updates, like the authentication of new blocks, are provided by the network of bitcoin miners at large. This item has been corrected. Cryptojacking is evolving. The private key is the important key, since it is required to access the bitcoins and the other keys can be generated from it. How does Binance stand against all these try-hard competitors? Each miner has a copy of the cryptocurrency specific blockchain and can validate and process transactions for that network. But the force that really makes the entire machine go is pure capitalistic competition. For one thing, the firm has a massive, global client base, unmatched by other exchanges. The blocks aren't assembled on the network there is no step B , but by the miners, who can choose whatever transactions they want. In an incident related to Bitcoin, a weakness in the random number generator allowed bitcoins to be stolen from Android clients. This proves that the signature is valid.
With these complications it took me a long time to get the signature to work. Miners do also collect per-transaction fees from Bitcoin users, but those are currently much smaller than the fixed per-block reward. If it took miners less does coinbase sell eth bitcoin miners th s 10 minutes on average to solve those 2, blocks, then the difficulty is automatically increased. But here we are. In the case of Bitcoin, the reward is Gavin Phillips. For example, if you forget the change address in a transaction, excess bitcoins will go to the miners as a fee. Regards, Nagu. Normal people use software [1] that hides what is really going on, but I wanted to get a hands-on understanding of qts crypto ecb announcement crypto Bitcoin protocol. GastevCC: Using a public ledger comes with some problems. If you lose your private key for instance by throwing out your hard driveyour bitcoins are lost forever. How to find peers The first step in using the peer-to-peer network is finding a peer. The webpage has a small piece of JavaScript containing the cryptojacking code. With this system, bitcoins are passed from address to address through a chain of transactions. Bitcoin mining normally uses special-purpose ASIC hardware, designed to compute hashes at high speed. If you get one byte wrong, bitcoins ico bitcoin cost in 2010 transaction is rejected with no clue as to where the problem is. In a standard transaction, the scriptSig pushes the signature generated from the private key to the stack, followed by the public key. In fact, it is one of the inputs that your computer feeds into the hash function, not the output it is looking. By performing several steps, anyone can verify that the transaction is authorized by B. Raw computing power requires investment in hardware. This encoding is preferred because it takes less space in the blockchain and network.



