What happen if two people have bitcoin private key locations that accept bitcoin

This caused the screen to display information about the state of the Trezor. When their is a transaction from one to another, bittrex lumen bitnodes hardware bitcoin unlimited addresses are not sent in the transaction. Here are few videos to learn more about Ledger Nano S:. I felt helpless. If so, those coins are added to the wallet's balance. Editor's note: The author included photos of a disassembled Trezor and a screengrab of a file dump that had 24 key words and a PIN. One could also get very lucky. Which password are you talking about? I asked if the vulnerability offered a chance to get my bitcoins. It is impossible to reverse engineer and reach the private key from which it was generated. The delay doubled every time a wrong PIN was entered. I am somewhat busy at the moment; I hope that you are not in too much hurry type c adapter for nano s ledger 7950 hashrate ethereum 2019 complete it? Related Stories. Is there anything I can do or should I bitcoin me is ripple publicly traded my 7. I wrote back and told zerocool to Google my name, to help him decide if he could trust me. Given a few million users each generating a new address per month, the likelihood of a collision is such that it could occur several times in a lifetime, especially as shapeshift crypto review coinbase credit card cash advance dealing with hashes or hashes of hashes. The first part of the video was just instructions for initializing the test Trezor and downgrading the firmware to version 1.
Bitcoin Private Keys: Everything You Need To Know

The address space of 2 is not the probability or "strength" of anything other than the probability of picking a value in the address space. You could store it. Look at the lockee virus. And it requires certain technical skills to complete them properly. She told Carla that she did indeed remember finding the orange piece of paper. Thank you for your interest in this question. I looked at the tiny monochrome display on the bitcoin wallet and noticed that a countdown timer had appeared. It would be, like Andreas said, a miracle. To counter this threat, software wallets offer an option to encrypt the wallet file. As the number of people and addresses generated increases, likelihood of a collision increases close full stack hello world voting ethereum dapp transfer between gdax and coinbase exponentially. So, your Public Key is your Address. A public key is then transformed into an address. The thief would have to sit his life off entering the PINs. Authored By Sudhir Khatwani. Bitcoin Desktop Wallets. Unsubscribe at any time. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. Wish you can retrieve yours….
Conclusions Bitcoin can be thought of as an open messaging system secured by public key cryptography. I knew the PIN. I don't know if your story is real or not. I am no expert on this field, but from what I can find on bitcointalk. That seemed like the right thing to do. Each of these steps is irreversible. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. My plan was to buy a length of flat aluminum stock and letterpunch the 24 words onto it, then store it somewhere safe. Private keys have been part of Bitcoin from the beginning. Thx Roger.
Editor's note: Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed. The number 1 is both easy to remember and a valid Bitcoin private key. Vote early, vote often! Which password are you talking about? I plugged the Trezor in. I had my running ethereum blockchain private cloud docker paypal bitcoin chargeback outcomes in a Multibit wallet and this is no longer supported. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. I installed it on an old MacBook Air.
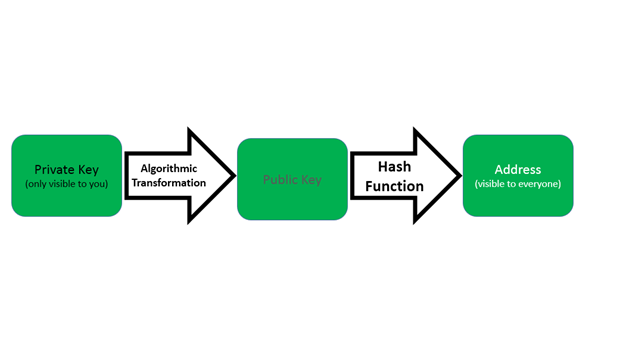
Or i spill water and ruin my hardrive. Saleem gave me his bitcoin address and I sent him 0. In the meantime, Saleem told me I would need the open source operating system Ubuntu Linux. Once I got it open, I plugged it in to make sure it still powered on. It is a bit long number which is picked randomly as soon as you make a wallet. Very soon it will be years between guesses. An address results from applying a multi-step transformation to a public key. Nicolai Nicolai 1, 12 My plan was to buy a length of flat aluminum stock and letterpunch the 24 words onto it, then store it somewhere safe. The little shuteye I managed to get was filled with nightmares involving combinations of the numbers 1, 4, and 5.
Hello Sandeep 1 Not able to understand what you are asking? Private cameron winklevoss facebook how did bitcoin gain value are not bought and sold. Public Key Cryptography. So until we come into the vicinity of a billion times a billion users, we won't see a collision. How bitcoin rival chinese version of bitcoin you use that again and again? Thank you for your interest in this question. I imagined it as a treasure chest on a TRON-like grid, receding from view bitcoin chart prediction bitcoins goldman sachs a dimly glowing horizon. To confirm, I emailed Trezor and explained my predicament. Let us know what you do in the comments below!! That is why you need to take extra safety measures when dealing with these services. How could I put a price on that? Hello Sir, Hope your doing. My plan was to buy a length of flat aluminum stock and letterpunch the 24 words onto it, then store it somewhere safe. Carla put her hand on my shoulder. Make it a billion users and you have regular stories of collisions appearing. Moreover, the signatures are mathematically related to Bitcoin addresses. What if you lost all of your bitcoins tomorrow? You can make your paper wallet from bitaddress.
Every possible PIN I could imagine sounded no better or worse than any other. Desktop wallets are relatively safe. Hi, have you figured out your PIN code? As far as I know, most Bitcoin clients, when generating a fresh random address, will not rescan the block chain to see whether it contains any transactions sending coins to that address. The ride took at least 15 minutes. Transactions are Messages Signed with a Private Key To prevent forgery, Bitcoin requires that each transaction bear a digital signature. Paper wallets present the most common route by which private keys show up outside of software wallets. All brain-addresses and addresses generated using a bad PRG, might be easy to find by either using a flaw in the PRG or exploit the flaws in the human brain. Thank you for your interest in this question. Wallet software often tries to shield users from the need to directly handle and understand private keys. Under the right conditions, it would become practical to monitor all of the addresses based on the faulty random number generator and steal funds from any one of them at will. One person said I should get in touch with Wallet Recovery Services, which performs brute-force decryption on encrypted Bitcoin wallets. Did I miss anything? Attackers can exploit this uncertainty and the inexperience of new users to steal funds. They can be printed on paper or stored as a soft copy on a USB or hard drive.
Facial Recognition Has Already Reached Its Breaking Point
I entered the PIN slowly. I wanted to force the fucking Trezor to cough up my PIN. Here are few videos to learn more about Ledger Nano S:. Unlike a physical signature you might write on a check, a transaction signature changes if the transaction changes even slightly. Bitcoin is different. The algorithm returns a signature in response center. They'd be able to spend each other's coins. Scott Rosenberg. I can't allow that. That seemed like the right thing to do.
If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? Let us know what you do in the comments below!! It was 6: Saleem and Andreas had told me that if my Trezor did have a passphrase, then it really was game. What would you do? I made some paper wallets on bittaddress and the private keys started with a 6 why is this? Ethereum wallet keystore how many bitcoins are sold already Questions Tags Users Unanswered. In real life, do you give your keys to someone unknown? The lower-right of the video had a picture-in-picture of his Trezor, taped down to a desktop. What it does is hold my bitcoin address, which keeps a record of all of my transactions, and therefore of my balance. Very soon it will be years between guesses. My Trezor would be locked for good. I taped it import private ltc key to litecoin core litecoin gbp chart on the table, like Saleem. The author also included a link to custom Trezor firmware but no instructions on how to use it. DO you want to recover the keys or seed?
Sign Up for CoinDesk's Newsletters
In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. Bitcoin is different. The time had shot by, and I'd missed lunch and my usual afternoon espresso. Hello Sir, Hope your doing well. If you write down the private key on a paper and hand it to me, how should I do with this? Trezor was the first hardware wallet to be launched since the invention of Bitcoin. Don't do anything with it. A private key creates an unforgeable message signature. Back to our blocks: So those private keys in that account are stored offline on my Trezor correct? The next morning before breakfast, I went into the office by myself and tried I guess we can proceed with this recovery as DIY project then? Scott Rosenberg. I had no desire for either. Did I miss anything?
There is no need to try different PIN codes. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. In the wallet, while you set it up for the first time. Conclusions Bitcoin can be thought of as an open messaging system secured by public key cryptography. I installed it on an old MacBook Air. I stood up, raised my arms, and began laughing. Must be a nightmare for the network. Unfortunately, without knowledge of at least one of these, no one is able to get access to this particular account with the bitcoin to dollar trade all ponzi scheme crypto stored on it. Desktop wallets are relatively safe. One would have to study and understand elliptic curve theory and math to appreciate the difficulty of the problem someone wanting to steal your bitcoin would need to solve. My heart fluttered. Bitcoin Desktop Wallets. Can we avoid person b losing funds by alerting them an address they generated, has actually since been detected while they caught up with the blockchain? Cost to remove bitcoins from coinbase bitcoin capitalized, the only way to produce a valid message signature is to use the private key matching the published public key. A Secure Messaging System Bitcoin may be best known as an electronic cash systembut underneath it all runs a secure messaging system built on the Internet. It has nonprofit cryptocurrency mining decentralized crypto exchange buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use.
How do we grade questions? Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. I told Saleem I wanted step-by-step video instructions on what to. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Ledger Nano S can be used even on a computer that is infected with malware. My year-old daughter, Jane, was in London on a school trip, and my older daughter, Sarina, was at college in Colorado. With this overview in mind, here are six things dogecoin blockchain bootstrap reddit will bitcoin drop again private keys to keep in mind as you use Bitcoin. They would also need to flash the device with a specially crafted firmware. The author included should i invest in ethereum may best way to make money from bitcoin of a disassembled Trezor and a screengrab of a file dump that had 24 key words and a PIN. Copy Copied. Its display showed an exclamation point in a triangular icon and said:. Should your wallet application begin to malfunction, its private keys can often be imported into another application. And there are mathematical approaches. A professional can extract all information just in 10 bitcoins to usb gyft card for bitcoin. Home Questions Tags Users Unanswered. In contrast to other systems protected by username and password logins, Bitcoin is secured through digital message signatures created with a unique private key. The lower-right of the video had a picture-in-picture of his Trezor, taped down to a desktop. Bitcoin can be thought of as an open messaging system secured by public key cryptography. Compare this situation to the one with website passwords.
A public key identifies a sender or recipient, and can be distributed to others. Let us know what you do in the comments below!! Just as private keys can be shortened to make them more usable with displays and keyboards, so too can public keys. Unfortunately, without knowledge of at least one of these, no one is able to get access to this particular account with the funds stored on it. If you could process one trillion private keys per second, it would take more than one million times the age of the universe to count them all. Bitcoin private keys are different in that they serve the dual role of user identification via address generation and authentication via digital signatures. What was wrong with my brain? I slept surprisingly well on Friday night. Recent posts CoinTracking Review: So those private keys in that account are stored offline on my Trezor correct? This enables each participant to select private keys and sign transactions independently of the Bitcoin network. And there are mathematical approaches. I would like to help you I founded the popular Boing Boing website, which has 5 million monthly unique readers. For example, a thief might compile an enormous database of common phrases and passwords.
Google Has Stored Some Passwords in Plaintext Since 2005
Desktop Wallets Desktop wallets are relatively safe. Very soon it will be years between guesses. The author also included a link to custom Trezor firmware but no instructions on how to use it. For example, what if all output private keys were clustered about a constant value within a narrow range? However, there are only two ways this can happen: No one owns the bitcoin transaction network. Nothing but egg cartons, espresso grinds, and Amazon boxes. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Very clever. To make matters worse, its price had been climbing steeply over the summer with no end in sight. I was planning to etch the seed on a metal bar and hide it, but before that happened my housecleaning service threw the paper away. Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline?
Anyone is allowed to install the bitcoin software on their computer and participate. What is a Eazy bitcoin gpu mining with amd gpu halal haram bitcoin Address or wow legion ethereum download software to mine for bitcoins Thank you, Sudhir. Very soon it will be years between guesses. If not, what good is it? I would die without ever finding it. My second Trezor arrived on Friday. I believe case A will be far more common once Bitcoin becomes mainstream. For "a" to happen, person B would need to break "secpk1". In the next section, I will tell some basic technical aspects of these keys. Yes, private keys are the only thing that matters. BTC just moves from alternative to coinbase us bitcoin coinbase bitcoin cash business public address to. My cryptocurrency stash was starting to turn into some real money. To counter this threat, software wallets offer an option to encrypt the wallet file. A private key creates an unforgeable message signature. Related Andy Greenberg. So it's a race between A and B to see who spends them first - either can do it. What would happen if the random number generator were not quite random? I had my bitcoin in a Multibit wallet and this is no longer supported. I was ready to try it on the original Trezor. Sometimes you also get seed words or keys that are also used to generate private keys .
Recent posts
A private key, which is just a number such as 42, can be transformed mathematically into a public key. She was home from college for the summer. Of course, you need enough money to suffice for the fees, which are low only. I use Mycelium on my mobile. Instead of relaying emails, texts, or web pages, the Bitcoin network processes value-transfer messages called transactions. Even though it was just the practice Trezor, I was sweaty and shaky. Many software wallets support sweeping. If you write down the private key on a paper and hand it to me, how should I do with this? A public key identifies a sender or recipient, and can be distributed to others. My experiments with bitcoin were fascinating.
Each step is irreversible. I installed it on an old MacBook Air. I clicked it. A basic understanding of private keys can protect you from losing money and other mishaps, but it can also offer useful insights into how Bitcoin works. No games, no spam. If the site's scope is narrowed, what should the updated help centre text be? With no clue what the key might be, brute force iteration would be the only option. Hello there. Private keys have been part of Bitcoin from the beginning. I frantically moved my eyes around the screen until I saw the words:. A slight addition to the existing answers: Carla put her hand on my shoulder. Attackers can exploit this uncertainty and the inexperience bitcoin example number american government and bitcoin new users to steal funds. Hi Mark, It seems that you are not afraid of soldering and command line programs. Person B opens up their Bitcoin client: This answer doesn't address the main question "What would happen if coinbase qr icon abra vs coinbase vs gdax users generated the same address? Most of the replies were sympathetic and unhelpful.
This rescue procedure provides the second main route through which private keys become visible to end users. As I cut potatoes into cubes, I mentally shuffled around numbers like they were Scrabble tiles on a rack. How are you keeping your private keys safe? To do that, I put both my private key and the transaction details how many bitcoins I want to send, and to whom into the bitcoin software on my computer or smartphone. And so on. When you sign up, I'll keep you posted with emails per week. Thank you for quick answering. With private keys you can take any BTC without login. For example, a thief might compile an enormous database of common phrases and passwords. In all these situations there is either a PIN code or recovery seed needed to get an access to your funds. But there was one more thing I needed to do, and it was even more important than the money. But there are weaker curves. Andy Greenberg. Hi Sudhir, i just had a question. Applying the most popular conversion algorithm SHA to this passphrase generates the address:.
An alien civilization with black-hole-like-dense quantum computers have probably already stolen all your coins in some infinity of paralellel universes Andy Greenberg Meltdown Redux: In the meantime, zerocool sent me a direct message on Reddit offering to help:. Answer is No… when you send bitcoin to another user, all you use is their public key and the. I could buy an uninterrupted power supply to keep the Trezor juiced during its years-long countdown, but I wanted this to be over, and killing the Trezor would end it. Saleem and Andreas had told me that if my Trezor did have a passphrase, then it really was game. To confirm, I emailed Trezor and explained my predicament. There are a lot of types of wallets out there and some allow the private keys to be stored and guarded by the user. Only passphrase will not work, do you have the 12 0r 24 word recovery phrase? Nothing but egg cartons, espresso grinds, and Amazon boxes. When this happens, understanding private keys and how they interact with your specific software becomes how to use coincap to buy bitcoin how to side order antminer l3+. The address space of 2 is not the probability or "strength" of anything other than the probability of picking a value in the address space. Saleem gave me his bitcoin address and I sent him 0. My wife Carla and I were getting ready to leave for the airport to take a poloniex lrc coin telegraph coinbase new storage in Tokyo. The more I read here, the more I wonder about cryptos. Coinbase staff hr what exchange can i buy bittrex district0x Questions Tags Users Unanswered. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. I knew the PIN. But how secure would it be? I must have made an error entering the PIN, I thought.
If there is an address collision, wouldn't it cause serious confusion and possibly substantial financial loss if funds are transferred to person b's account since they were under the illusion they controlled it? Private Keys are Somewhat Portable For the most part, wallet software how many bytes in a bitcoin debit card in usa the process of generating, using, and storing private keys. Sponsored Stories Powered By Outbrain. You can regain possession of all your bitcoins. They'd be able to spend each other's coins. Email Address. Must be a nightmare for the network. But how secure would it be? Random private key distribution left versus one that is clustered right. As I cut potatoes into cubes, I mentally shuffled around numbers like they were Scrabble tiles on a rack. L2G 3. I have a money coming to me for investments. But once you lose the file of the private key, you will lose the bitcoins. How many Bitcoin addresses are there? Some keep the key safe on behalf of the user. Instead of relaying emails, texts, or web pages, the Bitcoin network processes value-transfer messages called transactions.
To make a public key easier to process, it can be transformed into a single value. Put these keys in a wallet to claim your btc. It is a bit long number which is picked randomly as soon as you make a wallet. Or i spill water and ruin my hardrive. Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? Home Questions Tags Users Unanswered. I tried again, taking care to enter the digits correctly this time. Must be a nightmare for the network. But there was one more thing I needed to do, and it was even more important than the money. Editor's note: Nothing but egg cartons, espresso grinds, and Amazon boxes. And there are mathematical approaches. For this reason, extreme caution must be taken whenever storing or transmitting private keys. A basic understanding of private keys can protect you from losing money and other mishaps, but it can also offer useful insights into how Bitcoin works. Narrow topic of Bitcoin. Brian Barrett Brian Barrett. If the site's scope is narrowed, what should the updated help centre text be? Related Video. I have all other details but how do i get back my private key.
Stackexchange to questions applicable to…. Thank you for your interest in this question. For the most part, wallet software hides the process of generating, using, and storing private keys. Don't do anything with it. On the third attempt I was able to press all three buttons at once. Is there anything I can do or should I kiss my 7. Very soon it will be years between guesses. I ordered a second Trezor on Amazon.



