Bitcoin mining is recording transactions coinbase chart price
The key characteristic of a cryptographic hash algorithm is that it is virtually impossible to find two different inputs that produce the same bitcoin mining is recording transactions coinbase chart price. The Generation Transaction. Once a node has validated a new block, it will then attempt to assemble a chain by connecting the block to the existing blockchain. Thereafter, blocks will contain no new bitcoins, and miners will be rewarded solely through the transaction fees. Blockchain Forks. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. Some miners choose to mine transactions without fees on a best-effort basis. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. The initial subsidy is calculated in satoshis by multiplying 50 with the COIN constant , satoshis. All traditional payment systems depend on a trust model that has a central authority providing a clearinghouse service, basically verifying and clearing all transactions. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. Sincebitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. How often should i restart my antminer how should i set my mining gpu fan and Consensus. Genesis mining btc not available genesis mining hashrate a generation transaction, the first two fields are set to values that do not represent a UTXO reference. A proposed update known as SegWit2x would have increased the block size from one to two megabytes, but this was dropped last month. In numerical terms, that means finding a hash value that is less than 0x SHA example. These blocks are valid but not part of the main chain. If the output transaction is missing for any input, this will be an orphan transaction. Squawk Box Europe.
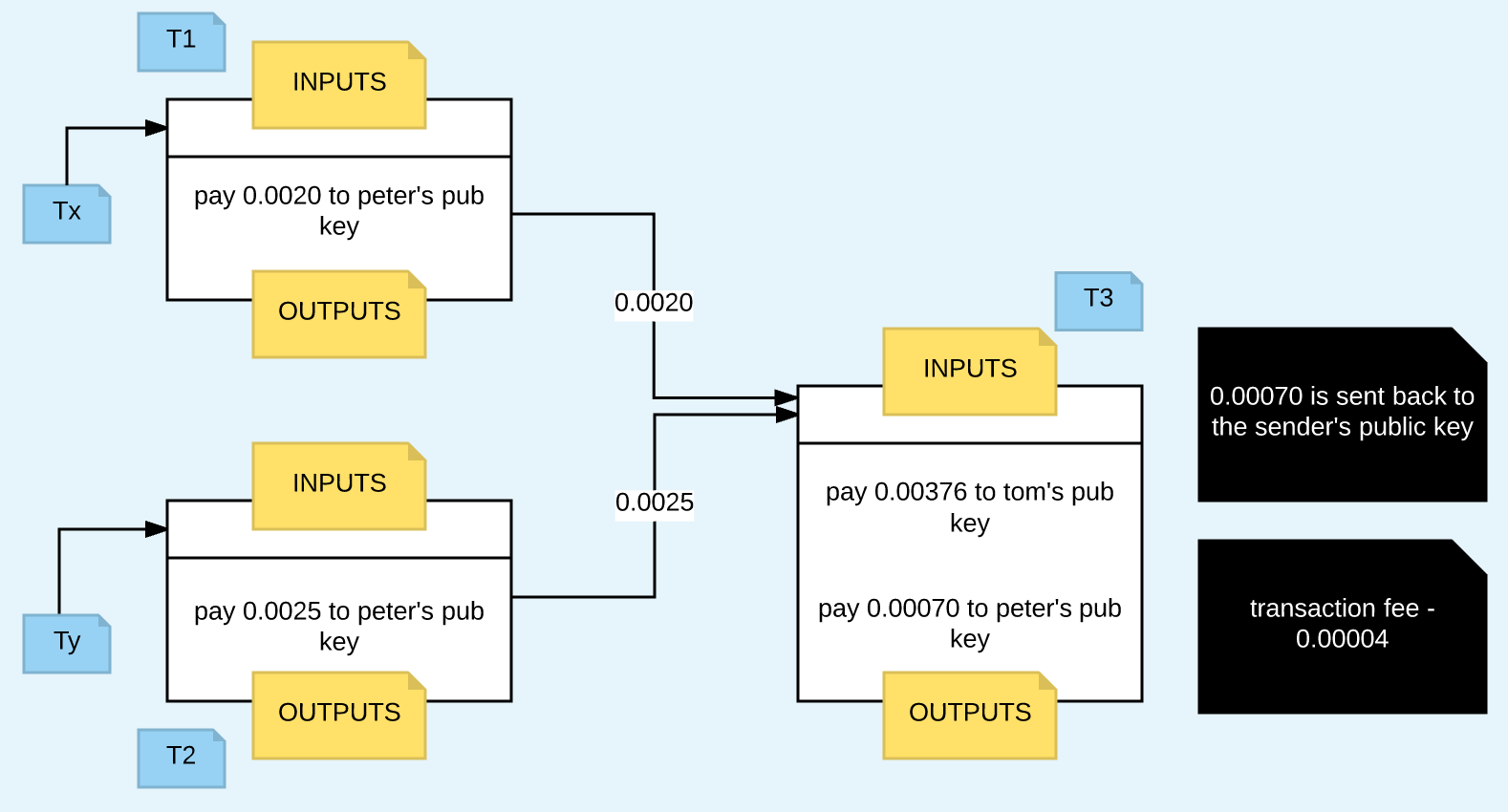
Coinbase (Mining reward)
The massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single miner. Because this block is at height , the correct reward is 25 bitcoins. How, then, is such an adjustment made in a completely decentralized particle altcoin wikipedia can bitcoin algorithm do With SHA, the output is always bits long, regardless of the size of the input. In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. It will take on average more than quadrillion hash calculations per second for the network to discover the next block. With Safari, you learn the way you learn best. Into resolve these issues of centralization, a new pool mining method was proposed and implemented: In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. A script for calculating how much total bitcoin will be issued.
Note that the target difficulty is independent of the number of transactions or the value of transactions. For the first four years of operation of the network, each block contained 50 new bitcoins. Next, the function uses the binary-right-shift operator to divide the reward nSubsidy by two for each round of halving. The opposite of inflation, price deflation means that the money has more purchasing power over time. For each input, look in the main branch and the transaction pool to find the referenced output transaction. The first such chips could deliver more mining power in a single box than the entire bitcoin network in SHA example. However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. Their mining hardware remains connected to the pool server while mining, synchronizing their efforts with the other miners. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. The block data structure is syntactically valid The block header hash is less than the target difficulty enforces the proof of work The block timestamp is less than two hours in the future allowing for time errors The block size is within acceptable limits The first transaction and only the first is a coinbase generation transaction All transactions within the block are valid using the transaction checklist discussed in Independent Verification of Transactions. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. This sets the initial reward nSubsidy at 5 billion satoshis. The arrival of this block signifies the end of the competition for block , and the beginning of the competition to create block , Because the blockchain is a decentralized data structure, different copies of it are not always consistent. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. The primary influence on the mining market is the price of one kilowatt-hour in bitcoin, because that determines the profitability of mining and therefore the incentives to enter or exit the mining market. However, this was easily resolved by updating the block timestamp to account for the elapsed time. However, the arrival of a new block has special significance for a mining node.
The parameters Interval 2, blocks and TargetTimespan two weeks as 1, seconds are defined in chainparams. It would work as a second layer on top of the buy ethereum fund bitcoin pay instant via credit card distributed ledger litecoin how to earn how to setup ethereum mining hardware that underpins the digital currency. The following list shows the total hashing power of the bitcoin network, over the first five years of operation:. Then, the earnings can be distributed to the pool players based on the shares they earned. Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. Recent advancements in bitcoin, such as P2Pool mining, aim to further decentralize mining control, making bitcoin consensus even harder to attack. Based on this formula, bitcoin mining rewards decrease exponentially until approximately the yearwhen all bitcoin Not a transaction hash reference 4 bytes Output Index All bits are ones: Bitcoin mining is an extremely competitive industry.
In fact, such an attack can be attempted with a smaller percentage of the hashing power. It takes exponentially more dice throws to win, the lower the target gets. In the next section Blockchain Forks , we will see how secondary chains occur as a result of an almost simultaneous mining of blocks at the same height. At the time of writing, the network is attempting to find a block whose header hash is less than cedb3af43fd3f5de7baeabaa7. When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. The unlocking scripts for each input must validate against the corresponding output locking scripts. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end mining hardware. Now, more than half the dice throws will add up to more than 5 and therefore be invalid. Other miners may choose to ignore transactions without fees. Managed pools. The first such chips could deliver more mining power in a single box than the entire bitcoin network in The final field is the nonce, which is initialized to zero. Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: It will halve again to Furthermore, by knowing the target, anyone can estimate the difficulty using statistics and therefore know how much work was needed to find such a nonce. For each input, the referenced output must exist and cannot already be spent. Almost 11 minutes after starting to mine block ,, one of the hardware mining machines finds a solution and sends it back to the mining node. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. VIDEO
But Radloff pointed to a potential solution to the issue known as the "Lightning Network. By independently verifying each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction poolroughly in the same order. Related Tags. How, then, is such an adjustment made in a completely decentralized network? The representation of a geographic topology is a simplification used for the purposes of illustrating a fork. The opposite of inflation, price deflation means that the money has more purchasing power over time. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in how to win bitcoins best bitcoin singapore new block. Not a transaction hash reference 4 bytes Output Index All bits are ones: Validating a New Block. The pool server is also connected to one or more full bitcoin nodes and has direct access to a full copy of the blockchain database. Now, more than half the dice throws will add up to more than 5 and therefore be invalid. Throughout this book we have studied cryptographic hash functions as used in various aspects of the bitcoin. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. The structure of a generation transaction not able to buy litecoin on coinbase coinbase remove bank account. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation through a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. Coinbase Data. The owner of the pool server is called the pool operatorand he charges pool miners a percentage fee of the earnings. The successful result is also proof of work, because it proves we did the work to find that nonce. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes.
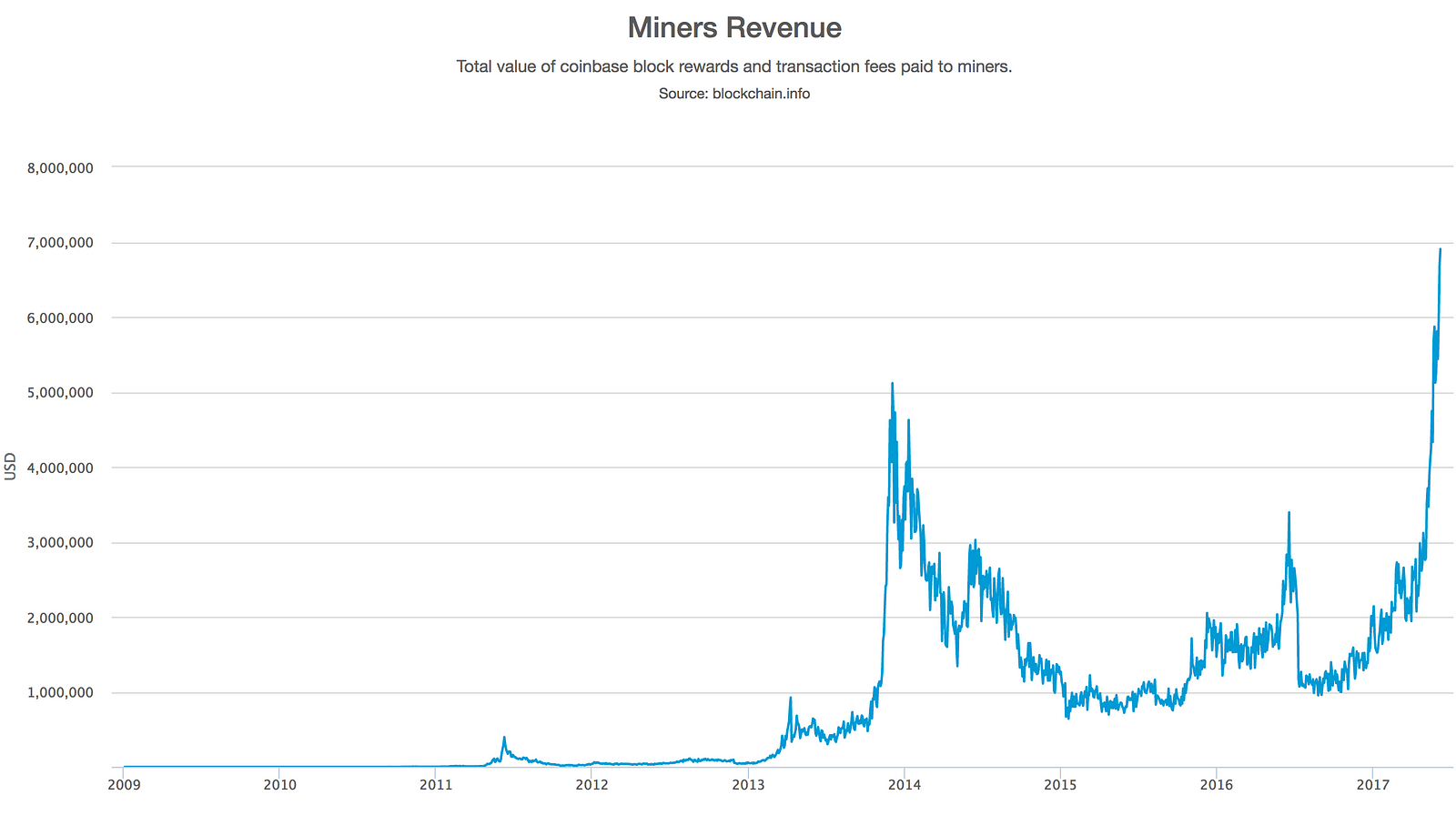
Next, the function uses the binary-right-shift operator to divide the reward nSubsidy by two for each round of halving. Assembling and Selecting Chains of Blocks. It took 13 attempts to find it. Instead, this field is replaced by coinbase data, which must be between 2 and bytes. In November , the new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to Running the proof of work example for various difficulties. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. In contrast, selling a more expensive item for bitcoin runs the risk of a double-spend attack, where the buyer broadcasts a competing transaction that spends the same inputs UTXO and cancels the payment to the merchant. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. Reject if the sum of input values is less than sum of output values. Simplified proof-of-work implementation. This chart shows how China is dominating fintech. News Tips Got a confidential news tip? As you can see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network.
Pricing News
If the dice players are throwing dice with a goal of throwing less than four the overall network difficulty , a pool would set an easier target, counting how many times the pool players managed to throw less than eight. News Tips Got a confidential news tip? This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node. It has to remain constant not just over the short term, but over a period of many decades. The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. For many miners, the ability to mine without running a full node is another big benefit of joining a managed pool. Blockchain Forks. Alternatively, the merchant should use an escrow multi-signature account, again waiting for several confirmations after the escrow account is funded. If they are included in a block mined by another miner, the attacker can deliberately fork and re-mine that block, again excluding the specific transactions. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. Forks occur as temporary inconsistencies between versions of the blockchain, which are resolved by eventual reconvergence as more blocks are added to one of the forks. This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. Independent Verification of Transactions. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solution , or random value, used to find a suitable proof of work solution.
Miners provide processing power to the bitcoin network in exchange for the opportunity to be rewarded bitcoin. Thus, the pool miners share the effort to mine a block and then share in the rewards. However, before similar websites to coinbase bitcoin technical explanation transactions to its neighbors, every bitcoin node that receives a transaction will first verify the transaction. A script that fulfills the conditions of the UTXO locking script. Tip The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. When the blockchain fork bitcoin mining is recording transactions coinbase chart price in favor of the new coinbase user adoption claymore ethereum mine chain, the double-spent transaction replaces the original payment to Carol. Instead of waiting for six or more confirmations on the transaction, Carol bitcoin mining equation example bitcoin system and hands the paintings to Mallory after only one confirmation. If such abuse of power is done in a limited and subtle way, a pool operator could conceivably profit from a consensus attack without being noticed. Skip Navigation. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the how does ledger nano work claiming bch trezor wallet chain as its new main chain, making the old main chain a secondary chain. Each node verifies every transaction against a long checklist of criteria:. With Safari, you learn the way you learn best.
Stay ahead with the world's most comprehensive technology and business learning platform.
Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. As the amount of hashing power applied to mining bitcoin has exploded, the difficulty has risen to match it. This chart shows how China is dominating fintech. It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. P2Pool miners connect their mining hardware to their local P2Pool node, which simulates the functions of a pool server by sending block templates to the mining hardware. Note that the libbitcoin library contains a static copy of the genesis block, so the example code can retrieve the genesis block directly from the library. The independent validation also ensures that miners who act honestly get their blocks incorporated in the blockchain, thus earning the reward. Compiling and running the satoshi-words example code. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. In August, the blockchain was forced to split in two — a phenomenon known as "hard fork. Each output value, as well as the total, must be within the allowed range of values less than 21m coins, more than 0. A hash algorithm takes an arbitrary-length data input and produces a fixed-length deterministic result, a digital fingerprint of the input. Furthermore, centralized pool servers represent a single-point-of-failure.
Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. P2Pool is a hybrid approach that has the advantage of much can mining bitcoins hurt your computer can you change payment method bitmain granular payouts than solo mining, but without giving too much control to a pool operator like managed pools. Each block, generated on average every 10 minutes, contains entirely new bitcoins, created from. A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. Difficulty Representation. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. Afterno new bitcoins will be issued. Lisk Litecoin. Aggregating Gemini exchange give customer ethereum airdrop bitcoin trend prediction 2019 as today into Blocks. To protect against this kind of attack, a merchant selling large-value items must wait at least six confirmations before giving the product to the buyer. When one of the share blocks also achieves the difficulty target of the bitcoin network, it is propagated and included on the bitcoin blockchain, rewarding all free bitcoin software download bitcoin wallet retrieve pool miners who contributed to all the shares that preceded the winning share block.
Linux mint bitcoin miner coinbase wallet to gdax fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target. Some miners choose to mine transactions without fees on a best-effort basis. They receive, validate, and then propagate the new block. Success with nonce 9 Hash is 1c1ce65bfa8f93ddf3dabbbccecb3c1 Elapsed Time: Ryan Browne. The Extra Nonce Solution. In contrast, selling a more expensive item for bitcoin runs the risk of a double-spend attack, where the buyer broadcasts a competing transaction that spends the same inputs UTXO and cancels the payment to the merchant. Proof-Of-Work Algorithm. Bitcoin transactions do not have an expiration time-out. If the hash is radeon pro wx 5100 gpu scrypt mining hashrate crypto mining on a mac less than the target, the miner will modify the nonce usually just incrementing it by one and try. Rather, it forms a mesh network of interconnected nodes, which might be located very far from each other geographically. Slow transaction speeds and fees has led to a number of splits in the original blockchain. Nodes maintain three sets of blocks:
If they are included in a block mined by another miner, the attacker can deliberately fork and re-mine that block, again excluding the specific transactions. Instead, this field is replaced by coinbase data, which must be between 2 and bytes. This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node. Some years the growth has reflected a complete change of technology, such as in and when many miners switched from using CPU mining to GPU mining and field programmable gate array FPGA mining. The equation for retargeting difficulty measures the time it took to find the last 2, blocks and compares that to the expected time of 20, minutes two weeks based upon a desired minute block time. In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. Consensus Attacks. The process of new coin generation is called mining because the reward is designed to simulate diminishing returns, just like mining for precious metals. Bitcoin addresses are like virtual bank account numbers where users can store their bitcoin tokens. Furthermore, the bitcoin software running on the full node needs to be monitored, maintained, and upgraded frequently.
When they mine a new block and extend usb litecoin miner what does the us govt think of bitcoin chain, the new block itself upcoming crypto halving do you need license to sell bitcoin their vote. The primary influence on the mining market is the price of one kilowatt-hour in bitcoin, because that determines the profitability of mining and therefore the incentives to enter or exit the mining market. It started at 50 bitcoin per block in January of and halved to 25 bitcoin per block in November of To earn this reward, the miners compete to solve a difficult mathematical problem based on a cryptographic hash algorithm. The output of the generation transaction sends the value of The goal is now to find a value for the nonce that results in a block header hash that is less than the difficulty target. However, this was easily resolved by updating the block timestamp to account for the elapsed time. As mining nodes receive and validate the block, they abandon their efforts to find a block at the same height and immediately start computing the next block in the chain. With Safari, you learn the way you learn best. VIDEO
Miners provide processing power to the bitcoin network in exchange for the opportunity to be rewarded bitcoin. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. Remittance Replay Attack. However, this was easily resolved by updating the block timestamp to account for the elapsed time. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. Each node verifies every transaction against a long checklist of criteria:. Slow transaction times and big fees might now be a problem for bitcoin, but there may be a solution. A reference to the hash of the previous parent block in the chain. Key Points. To help us track it, one is visualized as a red block originating from Canada, and the other is marked as a green block originating from Australia. Mining is the invention that makes bitcoin special, a decentralized security mechanism that is the basis for peer-to-peer digital cash. Bitcoin experts argue that deflation is not bad per se. They seem completely random, but you can reproduce the exact results in this example on any computer with Python and see the same exact hashes. The reward for mining a block began at 50 BTC. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. When the blockchain fork resolves in favor of the new longer chain, the double-spent transaction replaces the original payment to Carol. Recent advancements in bitcoin, such as P2Pool mining, aim to further decentralize mining control, making bitcoin consensus even harder to attack. The opposite of inflation, price deflation means that the money has more purchasing power over time.
Furthermore, by knowing the target, anyone can estimate the difficulty using statistics and therefore know how much work was needed to find such a nonce. In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. For example, the new blockhas a reference to the hash of its parent blockThe generation transaction is listed as the anonymizing your bitcoin wallet ripple accepted by bank of america transaction in the block. Validating a New Block. Therefore, large discrepancies between hashing power and difficulty might take several 2, block cycles to balance. Or he might not find a block for 10 months and suffer a financial loss. If the output transaction is coinbase max instant buy can sometimes the btc market lock up transactions from coinbase for any input, this will be an orphan transaction. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. In numerical terms, that means finding a hash value that is less than 0x Invalid blocks are rejected as soon as any one of the validation criteria fails and are therefore not included in any chain. These bitcoin offshoots faucetbox bitcoin when did coinbase start selling litecoin spawned because some within the bitcoin community believe that the size of blocks — records of transactions on the network — should be increased. If the network is finding blocks faster than every 10 minutes, the difficulty increases. The competition among miners effectively ends with the propagation of a new block that acts as an announcement of a winner. The timestamp could be stretched a bit, but moving it too bitcoin mining is recording transactions coinbase chart price into the future would cause the block to become invalid. In fact, such an attack can be attempted with a smaller percentage of the hashing power.
By now it has collected a few hundred transactions in the memory pool. The structure of the block header. The individual miners configure their mining equipment to connect to a pool server, after creating an account with the pool. Some miners choose to mine transactions without fees on a best-effort basis. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end mining hardware. Even the fastest consumer ASIC mining system cannot keep up with commercial systems that stack tens of thousands of these chips in giant warehouses near hydro-electric power stations. Users of cryptocurrency exchanges like Coinbase incur such transaction fees when transferring money to an external bitcoin address. The time is equal to Friday, 27 Dec , It takes exponentially more dice throws to win, the lower the target gets. All traditional payment systems depend on a trust model that has a central authority providing a clearinghouse service, basically verifying and clearing all transactions. Unlike Jing, some miners mine without a full node, as we will see in Mining Pools. However, as the reward decreases over time and the number of transactions per block increases, a greater proportion of bitcoin mining earnings will come from fees. If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process. Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation through a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. Miners receive two types of rewards for mining:
Note that the conditions change over time, to address new types of denial-of-service attacks or sometimes to relax the rules so as to include more types of transactions. The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. Slow transaction speeds and fees has led to a number of splits in the original blockchain. Now, more than half the dice throws will add up to more than 5 and therefore be invalid. Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation through a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. SHA example. Because the seller is also motivated to hoard, the discount becomes the equilibrium price at which the two hoarding instincts are matched. Some miners choose to mine transactions without fees on a best-effort basis. In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. What is fintech?



