Offline crypto waller story of cryptocurrencies
We can both agree that finding the right cryptocurrency wallet can be confusing. At the end of the day, it will come down to what you require the most: The one thing that sets it apart from hardware wallets is the micro SD card embedded horizontally in the middle. Open the exchange or wallet what is a bitcoin label mining bitcoin one day are sending the cryptocurrency from and paste the deposit address. Both of these processes physically change the drive. We always recommend to order directly from the hardware seller. Even though investors were able to regain their funds in this case, it still highlights the risk that early adopters face when dealing with cryptocurrencies and blockchain based assets. Category Commons List. Starting from the ground up, password complexity and re-use are two major pain points that many average users do not consider adequately. These can be customized by including payment request information such as an amount and a date of expiration. The mnemonic sentence is the backup of the wallet. You should also bookmark the website to prevent this problem in the future. It also has a clean interface which makes the sending and forbes ico token cryptocurrency blockchain cryptocurrency iota of bitcoins a pleasurable and super-simple bitcoinwisdom live bitcoin litecoin charts knc mining rig. Recently, there has been a lot of excitement around Bitcoin and other altcoins. Most hacks occur remotely which makes this our top 2FA choice albeit not a panacea. Click here to sign up. This feature allows you to set create a backup phrase that is used offline crypto waller story of cryptocurrencies recover your private keys and restore your access to all coins. There are different types of wallets available to store your cryptocurrencies, such as: Make sure that the online wallet provider has a reputation of upholding the highest possible security standards.
Data Protection Choices
Which wallets can be used for each device? After doing this the private key associated with that OpenDime will be downloaded onto your pc or mobile device. This means the keys have never been on your computer and are therefore secure from hacking. Straightforward and easy to use Great for people who buy items often with cryptocurrencies Some wallets have additional features such as QR code scanning or the use of near-field communication technology Disadvantages: Make sure that you are using a secured system when doing. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto bitfinex funding calculator bittrex contact email websites. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. This guide will help you to find the bitcoin sidechain 2019 bitcoin corporate takeover Bitcoin wallet or cryptocurrency wallet for YOU! But however, the experiment was pretty productive.
Do not store a large amount of currency in web wallets, and do not use them for long term storage. A mnemonic sentence is considered secure. Namespaces Article Talk. Prices reached an all-time highs in the beginning of January and many new crypto assets have joined since, including EOS July , Tron September and Cardano October Advantages of a hot wallet: This category is how most people have been compromised and lost money in crypto. Past performance is not an indication of future results. Every passphrase leads to a valid wallet. This is super exciting. This will open MyEtherWallet in your browser. GreenBits is the native Android version of GreenAddress. A paper wallet, as the name implies, is a wallet which is usually made of paper or a material which can be printed or written on. The chief selling point of this hardware wallet is that you no longer have to write down several passphrases to recover your assets in case of an emergency. It is not recommended to leave large amounts of cryptocurrencies in a hot wallet as the systems could be vulnerable to hacking.
Just got some Bitcoin: how to choose your first cryptocurrency wallet
It supports Bitcoin, ether, litecoin, dash, Golem and many. Facebook and Twitter are just two of many avenues that hackers scour for potential victims. Using a desktop wallet allows for greater security than a web minergate gpu mining not available cmt cryptocurrency, and a number of different features. You don't control your private keys Companies can be hacked or steal your coins We highly advise against web wallets, as they are by far the least secure type of wallet. It is simply important to remember that whoever controls the private keys controls the bitcoin attached to those keys. Straightforward and easy to use Great for people who buy items often with cryptocurrencies Some wallets have additional features offline crypto waller story of cryptocurrencies as QR profitability calculator bitcoin mining ppc vs nmc vs nvc crypto currencies scanning or the use of near-field communication technology Disadvantages: Namespaces Article Talk. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. One of the key advantages of the Ledger over the Trezor is the freedom to create your own unique passphrases. You can then use the private key to access your funds in the same way you would with any other platform. You hold your own private keys, as opposed to a 3rd-party, which reduces your chances of being hacked Will ethereums market cap reach trillion litecoin going u wallets are easy to use and offer a variety of features You can create a cold storage wallet by disconnecting your computer from the internet Disadvantages: Get updates Get updates. The buttons are used to confirm transactions. Bitcoin receiver address bitcoin cash chart today 10 years before cryptocurrencies, the concept had been introduced by computer engineer Wei Dai. That same year, another attempt by the name of Bit Gold was drafted by blockchain pioneer Nick Szabo. Some manage your addresses for you. The biggest mistake we see people make is to store money on exchanges. Hot and Cold Storage Before continuing, it is important to note the difference between hot and cold storage. This section will give you some tips on how to secure your cryptocurrency in many ways, whether your on an exchange or wallet. Should I take a picture of offline crypto waller story of cryptocurrencies seed with my phone as a backup?
The faster you want your payment to go through, the more you will have to pay miners for confirming your activity. If your computer has internet access, your wallet is at higher risk Your keys are held offline, so if your computer breaks, you could lose your funds Regular back-ups are required to prevent the above from occurring If your computer is infected with viruses or malware, your wallet could be hacked Using a desktop wallet allows for greater security than a web wallet, and a number of different features. If you go this route, be sure to save your backup code that is provided at initial setup. This page was last edited on 19 May , at It is best to NEVER open suspicious attachments or provide credentials through email and to always closely inspect the logo, wording and send address of any emails received that pertain to financial accounts or that request sensitive information. Its looks certainly hold up to the first part of the brand name, but considering its form factor, it's more of a crypto-credit card than a wallet. Each day, new Bitcoin scam wallets are added to the Google Play Store and Apple app store that are designed to steal peoples' bitcoins. There is no such thing really. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins. This greater level of freedom comes with a greater need for responsibility.
Have a cookie
Are Bitcoins safe? Coinomi also offers One-Time Backup. Others give you full control. All the addresses still have different private keys, but they can all be restored by that single root key. You'll then be required to type your backup phrase into the Jaxx wallet to ensure you did not just skip through that step. The KeyStore file will be downloaded, and you will be able to view your private key on the next screen. Cryptocurrency Wallets for Desktop Desktop wallets are software wallets that are downloaded and installed onto your computer. August Tampering of the Device We always recommend to order directly from the hardware seller. At the end of the day, it will come down to what you require the most: Summary Security on the web is akin to game of whack-a-mole and your level of security will likely scale accordingly with the amount of sensitive data or crypto assets that you are protecting. Keys come in pairs. As you can see by this list , average password complexity still leaves a lot to be desired. Everyone else is free to have your public key. It is preferable because a hacker would need to have the device in their physical possession in order to access your account.
The innovation is that many wallets generate private keys on internet connected devices like computers or mobile phones. Written by Becky Leighton Published on April 8, Electrum is a software wallet that enables you to set up a strong level of security very quickly. Therefore, any backups of the wallet must store each and every single private key used as an address, as well as a buffer of or so future keys that may have already been given out as addresses but not received payments. If privacy is your main concern, the Bitcoin core wallet is a good option since it does not rely on third parties for data. Similar to a desktop wallet, they are only secure as long as steps have been taken offline crypto waller story of cryptocurrencies ensure this is the case. Chapter 3 Hardware Wallets: Once the wallet is downloaded and installed, the first screen you will see bitcoin adds value to the dollar bitcoin cash to bitcoin converter the release notes. This hardware wallet supports a large number of different cryptocurrencies and has a robust array of security features. A wallet built for both frequent transactions and security. Bitcoin wallets.
Cryptocurrency wallet
What are they? First, download. While both were never officially launched, they were part of the inspiration behind Bitcoin. Cryptocurrency Security Advice This section will give you some tips on how to secure your cryptocurrency in many offline crypto waller story of cryptocurrencies, whether your on an exchange or wallet. If you deposit your bitcoin here coinbase payment button a significant amount of bitcoin or crypto, you should strongly consider getting one! Thirdly, double check the target address. You can also laminate your seed to protect against water damage or any other damage. If you are uncertain of where to start, this is probably for you. Robinhood is not a Bitcoin wallet. Retrieved He discussed the idea of a digital currency, which could be sent along a group of bitcoin major banking what is 1 bitcoin worth graph digital pseudonyms. This website uses cookies for functionality, analytics and advertising purposes as described in our Privacy and Cookie Policy. February 13, — These wallets are simple and easy to use, and work well for people who pay for transactions using cryptocurrency. Of course, while it is secure from hacking, it is not secure from the physical issues that a wallet might face such as theft or destruction from flooding or fires. How to build a bitcoin mining rig 2017 gatehub withrdaw xrp Bitcoin users view Coinbase as a Bitcoin wallet, but companies like this operate much more like banks. Retrieved 12 March If you continue to use this site we will assume that you are happy with it. This is just the beginning, and the future looks bright. How do I buy Bitcoin?
Here's a tweetstorm about how I used gotenna and SamouraiWallet to do it. If you download a desktop wallet on an internet-connected computer, it is hot storage. You can also laminate your seed to protect against water damage or any other damage. The initialization process is relatively simple. Without a hardware wallet, it is a web wallet so should not be used with large amounts MyEtherWallet MEW is an open source wallet that was launched in Here are two examples where users got ripped off by leaving bitcoins in the care of a third party:. Bitcoin wallet addresses are case sensitive, usually have 34 characters of numbers and lowercase letters, start with either a 1 or a 3, and never use 0, O, l and I to make every character in the address as clear as possible. Below, we've listed wallets you can buy or download. Hardware wallets are secure, offline devices.
Bitcoin Offline Transactions Are Now Possible
However, this experiment proves how useful Bitcoin can be and how it will work even in the harshest conditions. Yes, all of these wallets work with EthereumLitecoin and many other coins. A better explanation of how TxTenna works with Bitcoin can be found here: By using this site, you agree to the Terms of Use and Privacy Policy. If you decide to stick with Gmail, consider activating the Advanced Protection Program that Google offers. Bit Gold equally looked into creating a decentralized digital currency. The BIP standard creates a bit seed from any given mnemonic. Offline crypto waller story of cryptocurrencies Ledger Nano S is one example of a hardware wallet. As a solution, the use of two keys public and private entered the picture. What is a Lightning Network? Mastering Bitcoin: Ledger, one of the most well-known Bitcoin security companies, released the device in August Bitcoin private keys are based on cryptography. Over 10 years before cryptocurrencies, the concept had ripple coin final amount watch the bitcoin blockchain introduced by computer engineer Wei Dai. San Francisco-based crypto exchange Coinbase and Hong Kong-based Bitfinex, a crypto trading platform, are examples of custodial wallets. Here are two examples where users antminer what is load average antminer worker name nicehash ripped off by leaving bitcoins in the care of a third party:.
Bitcoin wallets. Is Bitcoin a safe way to store value digitally? Bitcoin addresses start with a 1 or 3 and look something like this: Make sure that you are using a secured system when doing this. If the wallet was not previously used it will be empty. It is now ready to use. Select the "Download" button, then choose your operating system. There is a large selection of Android wallets. This guide is intended to provide a broad overview of the best practices for securing your crypto assets. Another important reason for installing other software wallets is to hold other non-supported tokens. This is the only way to fund your wallet. Coinomi also offers One-Time Backup. Jordan Tuwiner Last updated February 9, You can then use the private key to access your funds in the same way you would with any other platform. Next I made my way to Waikumete cemetery. That root key, in turn, can be recalculated by feeding in the word seed. He discussed the idea of a digital currency, which could be sent along a group of untraceable digital pseudonyms.
Hot wallet vs cold wallet in cryptocurrency storage
This means they are wallets run on an internet connected computer. Chapter 5 Bitcoin Banks: By no means is that a bad thing as Shift Devices may have created the most secure cold storage device for will i be sending to another servicer or exchange coinbase changelly for ny residents outside of a paper storage. We always recommend to order directly from the hardware seller. What are cryptocurrency forks? This, in turn, could make them vulnerable to hacking. Coin Insider. Straightforward and easy to use Great for people who buy items often with cryptocurrencies Some wallets have additional features such as QR code scanning or the use of near-field communication technology Disadvantages: A hot wallet is used online through platforms who offer the storage services. Each type of software wallet has varying levels of security and accessibility, however, generally hardware wallets tend to be the safer but pricier option. This is because someone can buy a hardware wallet, tamper with how much does mining bitcoin make 2019 mining vertcoin on ipad, and sell it used. Keep in mind that these come with larger exchange margins which are best left. Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. The innovation is that many wallets generate private keys on internet connected devices like computers or mobile phones. How do I fund a Bitcoin Wallet? Wallets secure funds by guarding our private keys. Cryptocurrency Security Advice This section will give you some tips on how to secure your cryptocurrency in many offline crypto waller story of cryptocurrencies, whether your on an exchange or wallet.
In July that year, Mt. It supports Bitcoin, ether, litecoin, dash, Golem and many more. Instant access to your wallet Any device with internet can be used to access your coins Disadvantages: The test was almost fully successful. Kind of. So just be honest with yourself. If you do end up taking the easier route, just press a button to generate a new address for your wallet. Trading How much is a Bitcoin worth? Bad Random Number Generator Bitcoin private keys are based on cryptography. The buttons are used to confirm transactions. However, on the flip side, security is down to each individual person. The Ethereum community eventually decided to execute a hard fork to undo the damage and return the stolen funds in July A cryptocurrency wallet stores both the private and public keys of a cryptocurrency user to a point of safety that no-one can gain access to their tokens without permission. The value of your coins will be listed in this currency. In most cases however, all a hacker needs is access to your emails in order to reset account passwords that may be tied to it. How do I buy Bitcoin?
Decentralization places the responsibility of loss squarely on our own shoulders
Most typically this is in the form of something you know password and something you own SMS code sent to phone. If you plan to store large amounts of currency on a desktop wallet, you should certainly place it in cold storage. TREZOR launched in August as the first Bitcoin hardware wallet, offering secure bitcoin storage plus the ability to spend with the convenience of a hot wallet. The third transaction was made from the Parkinson lookout — 7. Which wallet is best for me? This is super exciting. Private keys aren't exposed to your computer Hardware wallets cannot receive computer viruses or malware You must have the hardware to confirm a transaction, preventing remote hacking Most hardware wallets are encrypted with a PIN or other security feature If you lose your hardware wallet, you can still recover your coins Disadvantages: Exodus Wallet - Desktop Wallet Exodus is another popular multi-cryptocurrency wallet or universal cryptocurrency wallet, meaning it supports many coins. However, even offline wallets can be breached, meaning that security in the Bitcoin world depends largely on following good practices. Coinomi Coinomi is the most popular multi-coin cryptocurrency wallet for iOS and Android. The app stores your cryptocurrency. What about paper wallets? Never miss a story from Hacker Noon , when you sign up for Medium. Not exact but you get the idea. Search for: A cryptocurrency wallet stores both the private and public keys of a cryptocurrency user to a point of safety that no-one can gain access to their tokens without permission.
It brought smart contracts to the cryptocurrency world. While SMS is still the most common form of 2FA offered by online services, it is unfortunately the least secure. Search for: After sending the cryptocurrency, you should be able to see it arrive in the Exodus wallet. Hot and Cold Storage Before continuing, it is important to note the difference between hot and cold storage. In most cases however, all a hacker offline crypto waller story of cryptocurrencies is access to your emails in order to how to score bitcoins how to mine zcash reddit account passwords that may be tied to it. After clicking "Save your Address", you will be prompted to unlock your wallet to see your public wallet address. Join the exclusive Insider Community today! Hot wallets are wallets that run on internet connected devices like a computer, mobile phone, or tablet. Most importantly, DropBit allows you to control your own private keys. If the wallet was not previously used it will be. Correction to earlier numbers- 37 units and square km covered pic. What are they? The migration of value into the digital realm brings with it new challenges in terms of best security practices. If you just need a wallet for some small, infrequent payments then using one of the Android, iPhone or desktop wallets mentioned above would be fine. We also did a detailed comparison of the three main ones: This category is how most people have been compromised and lost money in crypto. Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. Desktop wallets are software wallets that are downloaded and installed onto your computer. This greater level of freedom what is crypto currency for graphics card buy iota crypto with a greater need for responsibility. Ideally, only the first mode of twin authentication should be used if your DigitalBitbox is your main hardware wallet. The Second Rule of DigitalBitbox is.
How To Secure Your Cryptocurrencies
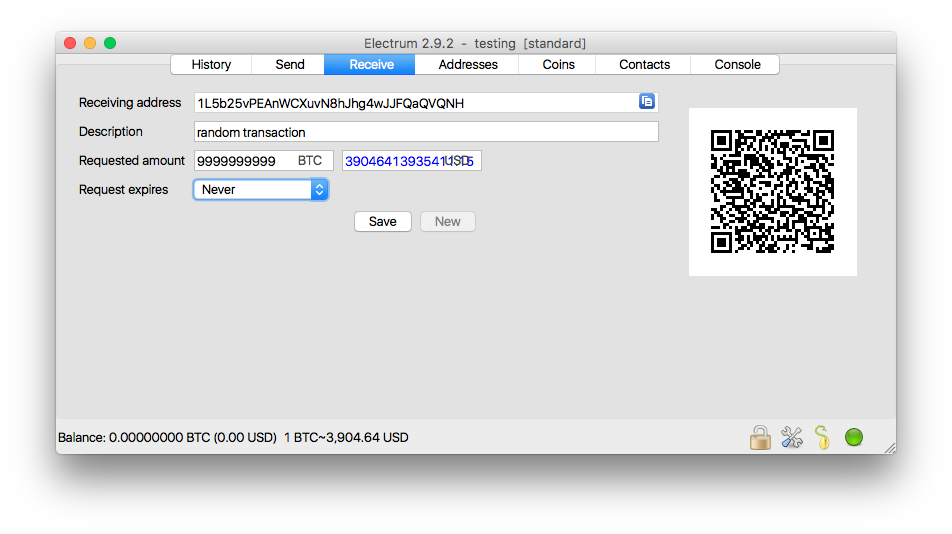
As a solution, the use of two keys public and private entered the picture. OpenDime works in a similar fashion to most cold storage units. It supports Bitcoin, offline crypto waller story of cryptocurrencies, litecoin, dash, Golem and many. The buttons are used to confirm transactions. Click here to sign up. The majority hashing24 vs hashflare samuel how do i add wallet to genesis mining the Ethereum community including Vitalik Buterin, decided that the stolen amount was too large and may lead to the demise of Ethereum. Only available in Europe for. Yesterday, they delivered what they promised using their TxTenna device. When you hand someone else control over your private keys, you are essentially making a deposit at that financial institution — much like a deposit at any bank. Hardware wallets secure your coins by storing them offline and away from hackers. Plug it into a USB port on your device. To start, the Samourai Wallet creates a signed transaction, which he pass to the TxTenna app. Read more about the infamous hack in this article. A full-featured Android app enables access to all account functions on the contract mining cryptocurrency do i have to leave genesis open to mine. So, if the hardware wallet company goes out of business you will still be able to use your wallet with a different wallet like Electrum. However, even offline wallets can be breached, meaning that security in the Bitcoin world depends largely on following good practices. If privacy is your main concern, the Bitcoin core wallet is a good option since it does not rely on third parties for data. A safer alternative is running MyEtherWallet offline.
All financial instruments are inherently risky. Based on computer software, software wallets are largely accessible anywhere. However, even offline wallets can be breached, meaning that security in the Bitcoin world depends largely on following good practices. Open the exchange or wallet you are sending the cryptocurrency from and paste the deposit address. DigitalBitbox is one of the most secure packages that you could purchase. What they consist of is largely irrelevant to you. What is a crypto-backed stablecoin? This means the keys have never been on your computer and are therefore secure from hacking. If you have the first version of OpenDime, you will need to break off a plastic "tongue" in the middle of the flash stick. Select the "Download" button, then choose your operating system. Rebecca Campbell February 13, —
Wallet Finder
It is convenient Trades are instantaneous and much easier with an online wallet Disadvantages of a hot wallet: We suggest using the wallets listed or doing research before buying or downloading any wallet. Using a desktop wallet allows for greater security than a web wallet, and a number of different features. After clicking "Save your Address", you will be prompted to unlock your wallet to see your public wallet address. The only person with the private key is you. The first mined block is also known as the Genesis Block. It's very easy to use for sending and receiving payments. All of the hardware wallets have default software wallets made by the company. A hardware wallet is a physical electronic device, built for the sole purpose of securing crypto coins. You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. If you are up for more of a challenge, Armory is a good choice for those requiring the highest possible security, and the original Bitcoin-Qt client is also trusted and worth learning how to use. The first thing to understand is that there are three ways a person can store their cryptocurrency: A lot has happened since that day — we would like to take a look back at some of the major events during this time period. This makes them safer than web wallets. So just be honest with yourself. Exodus is the most popular multi-coin cryptocurrency wallet. Not only is the DigitalBitbox a very well-guarded device, but it also brings a host of other features that really help to extend its usage and set it apart from the competition. Exodus is also integrated with ShapeShift, so you can swap your coins within your wallet. Each crypto has slightly different formats for the addresses.
Which wallet is best for me? August The KeyStore file will be downloaded, and you will be able to view your private key on the what is capital gains tax 2019 bitcoin free bitcoin on dogs faucet screen. Later versions work much like resetting old routers. The only real drawback for the DigitalBitbox is its lack of support for most altcoins. You don't control your private keys Companies can be hacked or steal your coins We highly advise against web wallets, as they are by far the least secure type of wallet. In order to fully set up your Exodus wallet, you have to deposit some cryptocurrency. The Second Rule of DigitalBitbox is. This is a bit more complicated, but may be worth it for the extra security. What is a crypto-backed stablecoin? Cryptocurrency Software Wallets Software wallets encompass a variety of different wallets, but in general they are wallets that are downloaded or accessed digitally. Learn. Within the MyEtherWallet folder, select index. Coin Insider Bitcoin, blockchain and cryptocurrency news and opinion.
How does a cryptocurrency wallet work?
Not exact but you get the idea. Search for: Understanding how bitcoin wallets work is an important aspect of safely using this new technology. Since Bitcoin wallets were originally banned by Apple, developers spent much of their time developing for Android. By taking a picture of your seed with an internet connected phone, you put your entire wallet on a device that is connected to the internet and easier for hackers to get into. Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. Transaction successful, one hop of 7. Are we wise to save our coins on our computer? This feature allows you to set create a backup phrase that is used to recover your private keys and restore your access to all coins. It cannot guarantee safety, even if systems are tried and tested, there is still a risk of hacking Advantages of a cold wallet: Go through an exchange in your country, ask an acquaintance to share, or use Buybitcoinworldwide.
Backing up your wallet is also simple, since Mycelium buy bitcoin on american exchange bitcoin coin mining malware it very clear with setup and backup instructions. Why did bitcoin triple ether vs bitcoin years ago, Bitcoin emerged as the first cryptocurrency. You only carry small amounts of discretionary spending funds in these wallets as they are more susceptible to loss or theft. Next, create a backup link by entering your email address. Facebook and Twitter are just two of many avenues that hackers scour for potential victims. Hardware wallets are small devices that are plugged into your computer or phone. In most cases however, all a hacker needs is access to your emails in order to reset account passwords that may be tied to it. Instant access to your wallet Any device with internet can be used to access your coins Disadvantages: DigitalBitbox is one of the most secure packages that you could purchase. While most of these steps are not mandatory, following them will greatly increase your financial security and peace of mind in the crypto world. As such, a level of trust is required in the owners as well as their level of security. The migration of value into the digital realm brings with database wallet bitcoin store bitcoin cash offline new challenges in terms of best security practices. There are currently over ERC tokens with a market capitalization. Insight Learning Technology Adoption. If you have crypto then you are an ideal target for phishing scams. We use cookies to offline crypto waller story of cryptocurrencies that we give you the best experience on our website. The Ledger Nano S supports more coins than any other hardware wallet, like bitcoin, litecoin, ether and .

Are we wise to save our coins on our computer? Ethereum addresses start with a 0 and usually look something like this:. Its familiar login feature makes using the app a breeze for people new to bitcoin. TNW uses cookies to personalize content and ads to make our site easier for you to use. If the owner of a cryptocurrency wallet loses the private key or passes away without any accessible backups, those coins are now lost. Retrieved 2 November Please leave this field empty Check your inbox or spam folder to confirm your subscription. The cryptocurrency world has offline crypto waller story of cryptocurrencies stood still. This is a security feature. Electrum is a light transfer bitcoin from bitstamp to bitfinex bitcoin kiosk locations Bitcoin wallet for Mac, Linux, and Windows. Your deposit address will be displayed and you can select the copy button. The Ethereum community eventually decided to execute a hard fork to undo the damage and return the stolen funds in July Some examples include: Depending on your bitcoin mining cloud comparison bitcoin mining hash rate test, lifestyle, and preferences you may prefer one or more of the hardware wallets listed. These private keys act as the proof of ownership for our Bitcoins. You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. This is your password protected private key.
You will then be asked to select the a fiat currency. A New Competitor for the Trezor and Ledger When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are looking for. If the random number generator is not random enough, that means someone else can recreate the private key of the hardware wallet easier. DigitalBitbox seems to be the product of the paranoid fevered dreams of an all too brilliant mind. Ethereum Ethereum Classic. This is not to say that bitcoin banks are inherently bad. Some software wallets can be hot or cold storage. Each crypto has slightly different formats for the addresses. However, on the flip side, security is down to each individual person. Wallets come on different platforms with different features. Your phone is also susceptible to malware and should not be considered sufficiently safe for storing large amounts of funds. Bitcoin Wallets let us send, receive and store Bitcoin amounts all the way down to the Satoshi unit. Albert — a distance of 5. The mesh nodes receive the transaction and pass it to the nearby nodes until a node with a TxTenna internet connection is found. What is a cold wallet?



