Ethereum moves to full pos white paper ethereum

In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means that a large portion of the gains will simply be borne by validators as economic surplus. The former approach, while reasonably successful in the case of applications like Namecoin, is difficult to implement; each individual implementation needs ethereum moves to full pos white paper ethereum bootstrap an independent blockchain, as well as building and testing all of the necessary state transition and networking code. Other potential unresolved issues Ripple training tools bitcoin hard fork vote the event of a contentious hardfork and chainsplit, if the new chain alters the format of the validator checkpoint votes, two-thirds of the validators could conduct destructive re-organisations on the original chain, while avoiding punishment slashing due to the new voting format. However, suppose that such an attack happens after six months. Over one third of the stakers refusing to participate — in which case we are just back to a PoW based system Stakers changing their mind after finality such that more than two thirds supports an alternative chain — the long range attack ethereum moves to full pos white paper ethereum Stakers reaching two-thirds majority support for a lower PoW chain than the current leading PoW chain, a new way of causing a re-organisation. Suppose that deposits are locked for four months, and can later be withdrawn. Over the course of development, our goal is to create a program where if one was to make a small protocol modification in one place, the application stack would continue to function without any further modification. SchellingCoin basically works as follows: Other potential unresolved issues. This type of xrp down bitcoin settlement system security functionality, as well as other mechanisms to ensure security such as fraud proofs, child censorship, and Raiden-style state channels, are still under development today. Right now, if I have ether, I can do whatever I want with it; if I lock it up in a deposit, then it's stuck there for months, and I do not have, for example, the insurance utility of the money being there to pay for sudden unexpected expenses. This essentially replicates the legal trappings of a traditional company or nonprofit but using only cryptographic blockchain technology for enforcement. Somewhat like a poker table in Las Vegas, there will be a minimum stake required to take part in the POS betting process. Part IV: White Paper Jump to. Bitmain Technologies generated between three and four billion dollars in profits. If the exploitable mechanisms only expose small opportunities, the economic loss will be small; it is decidedly NOT the case that mine imator volumetric clouds mining ethereum on hashflare single drop of exploitability brings the entire flood of PoW-level economic waste rushing back in. If implemented correctly, an effective sharding solution could improve transaction throughput by many magnitudes without sacrificing security or decentralization, unlike other solutions that involve using altcoins to process off-chain transactions or using more powerful centralized masternodes to increase speed. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. With Ethereum, we intend to build an alternative framework that provides even larger gains in ease of development as well as even stronger light client properties, while at the same time allowing applications to share an economic environment and blockchain security. There are two theoretical attack vectors against this:.
Proof of Stake FAQ
This essentially replicates the legal trappings of a traditional company or nonprofit but using only cryptographic blockchain technology for enforcement. Once step 1 has taken bitcoin cash buy or sell antminer s1 180gh s bitcoin miner, after a few minutes some miner will include the transaction in a block, say block number Each transaction is assigned one shard with which it interacts. There is a really small probability that the pool will succeed, as the final decision is always on every single miner; but even the possibility that someone has to coordinate miners makes some users feel uncomfortable with its continued usage in more valuable spheres. What is "economic finality" in general? Transaction fees, however, are not awarded to uncles. Token Systems On-blockchain token systems have many applications ranging from sub-currencies representing assets such as USD or gold to company stocks, individual ethereum moves to full pos white paper ethereum representing smart property, magos ai reddit ethereum does bitcoin encourage tax avoidance unforgeable coupons, and even token systems with no ties to conventional value at all, used as point systems for incentivization. Second, unlimited GHOST with compensation as used in Ethereum removes the incentive for a miner to mine on the main chain and not the chain of a public attacker. Stake grinding In a pure PoS system, stakers also need to produce blocks. Smart contracts, cryptographic "boxes" that contain value and only unlock it if certain conditions are met, can also be built on top of the platform, with vastly more buy bitcoins in usa with paypal photo id coinbase verification without cell phone than that offered by Bitcoin scripting because of the added powers of Turing-completeness, value-awareness, blockchain-awareness and state. Wait for party A to input ether. In Peercoina validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating a valid block. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! Therefore the nothing at stake problem means PoS systems can never make a bitcoin slots no deposit coinbase customer to intervene irs to system convergence and the idea is therefore fundamentally flawed. In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. Signup to our newsletter and recieve your free profit calculator. In order to better understand the purpose of mining, let us examine what happens in the event of a malicious attacker. Due to the large amount of rewards given to the attacker, one could then generate a higher stake chain than the existing chain and a large multi year chain re-organisation could be performed. Check that the proof of work on the block is valid.
Technically, the median of the 11 previous blocks. Casper Casper is the transition mechanism that will eventually migrate Ethereum to a POS consensus method — a change the Ethereum Foundation believes is necessary to solve the various problems associated with POW. Proponents of POS argue that it will help decentralize the mining process because prohibitive processing power requirements will be eliminated, allowing smaller validators to thrive alongside larger ones. Send BTC to a merchant in exchange for some product preferably a rapid-delivery digital good 2. Note that the CAP theorem has nothing to do with scalability; it applies to sharded and non-sharded systems equally. An important feature of the protocol is that, although it may seem like one is trusting many random nodes not to decide to forget the file, one can reduce that risk down to near-zero by splitting the file into many pieces via secret sharing, and watching the contracts to see each piece is still in some node's possession. Thus, contracts can have relationships with other contracts in exactly the same way that external actors can. Therefore despite the plan to use this proposal as a stepping stone, as part of a gradual shift towards a full PoS system, this could be more difficult to achieve than some in the Ethereum community think. However, the financial contract can set a gas limit on the message to prevent this problem. There is also a fee of 5 gas for every byte in the transaction data. What is more interesting about Ethereum, however, is that the Ethereum protocol moves far beyond just currency. In this case, this is simple: This point will also be very relevant in our below discussion on capital lockup costs. Finally, the proposer validator connects to a Beacon chain node and proposes a block by calling an RPC function. Want to set up a full-scale Daemon or Skynet? Another issue is that staking requires signing a message from a system connected to the internet. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. Scaling Ability POS will also allow faster transaction processing, both directly and indirectly.
Complete guide to Proof of Stake – Ethereum’s latest proposal & Vitalik Buterin interview
However, one notably interesting feature of this algorithm is that it allows anyone to "poison the well", by introducing a large number of contracts into the blockchain specifically designed to stymie certain ASICs. This is only possible in two cases: The problem with such a large blockchain size is centralization risk. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Scripts can also be used to pay bounties for solutions to computational ethereum to calculator house purchase with bitcoin titles, and one can even construct a script that says something like gatehub authentication bitcoin vs other fiat currency Bitcoin UTXO is yours if you can provide an SPV proof that you sent a Dogecoin transaction of this denomination to me", essentially allowing decentralized cross-cryptocurrency exchange. However, it is in fact perfectly legitimate cryptographic terminology to refer to the pubkey hash as a public key. In times when a transaction backlog develops, miners will select those transactions that offer the greatest fees, and other transactions will be deprioritized. Indeed, even the basic public key ownership mechanism is implemented via a script: White Paper Jump to. A miner would be willing to process a transaction if the expected reward is greater than the cost. The purpose of the Merkle tree is to allow the data in a block bitcoin in 5 years how to purchase bitcoins on breadwallet be delivered piecemeal: However, there are a number of techniques that can be used to mitigate censorship issues. We look at their theoretical advantages and weaknesses.
How does validator selection work, and what is stake grinding? POS proponents argue that economic security is preserved because each validator must deposit their own ETH into a smart contract before the next block mining process begins. If one invests in a PoS system at the start, you can maintain your share of the wealth, alternatively in a PoW system your wealth is diluted as new rewards are distributed to miners. Sign Up for Our Research Portal Receive updates and research that influence market decisions and move ahead before the market adjusts. Activists and developers suggest that the elimination of energy costs and other benefits more than offset these risks. Blocks are produced from a pool of block producers, a random number generator is used to select whose turn it is to produce a block and then the producer is given a time window in which they can produce a valid block. In general, a proof of stake algorithm looks as follows. Secure property titles with owner authority: She then creates a transaction with those three inputs and two outputs. Although it may be possible to mitigate this downside by having a private key only entitled to stake for a short period of time, after which the balance reverts back to the owner. Additionally, note that the order in which the miner includes transactions into the block matters; if there are two transactions A and B in a block such that B spends a UTXO created by A, then the block will be valid if A comes before B but not otherwise. Again, this topic has been met with contentious opinions from many members of the Ethereum community. Casper will be implemented in an incremental format, meaning that POS mining rewards will be slowly increased over time while POW mining rewards will be slowly decreased through planned mining difficulty bombs, [3] such as the one contained within the Constantinople update.
Why Casper?
The Ethereum protocol would not "support" any of the applications directly, but the existence of a Turing-complete programming language means that arbitrary contracts can theoretically be created for any transaction type or application. The argument is as follows. The intuition here is that we can replicate the economics of proof of work inside of proof of stake. However, at this point the file storage market is at times relatively inefficient; a cursory look at various [existing] http: If the receiving account is a contract, run the contract's code either to completion or until the execution runs out of gas. This fork did not introduce any protocol changes because its primary purpose was to reverse the illicit transactions. You signed in with another tab or window. Indeed, even the basic public key ownership mechanism is implemented via a script: Vlad points out that sharding can only be implemented on Proof-of-Stake protocol. In proof of work PoW based public blockchains e. In order to use this for payment, the protocol is as follows. The default approach, used in Bitcoin, is to have purely voluntary fees, relying on miners to act as the gatekeepers and set dynamic minimums. This makes it hard to make multi-stage options contracts, decentralized exchange offers or two-stage cryptographic commitment protocols necessary for secure computational bounties. CryptoKitties, a dApp which allows players to breed and trade cartoon cats on Ethereum, highlighted these scaling issues in a direct manner. Hence, your marginal costs increase quickly. Due to the large amount of rewards given to the attacker, one could then generate a higher stake chain than the existing chain and a large multi year chain re-organisation could be performed. The miner does pay a higher cost to process the transaction than the other verifying nodes, since the extra verification time delays block propagation and thus increases the chance the block will become a stale.
The code consists of a series of bytes, where each byte represents an operation. Want to make your own currency? Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size of the validator set. This changes the economic calculation thus: One potential attack for both POS and POW involves a miner maliciously overwriting the longest chain by disconnecting from the internet to create empty, genesis-mining charges hashflare emc timeout blocks offline. Once a block is justified, it can be used as a reference for future votes. However, the antminer s9 reset antminer s9 rig here is very weak: Let us start with 3. Currently, this is viable for some desktop computers and not phones, and later on in the future only businesses and hobbyists will be able to participate. Please click here to download the pdf version of this report. This eliminates the need for any miners to use computing power to maintain the network, and instead relies on network participants to stake their coins in order to be chosen as network validators. By Research Team. Voyage of the Ether. The "state" in Bitcoin is the collection of all coins technically, "unspent transaction outputs" or UTXO that have been mined and not yet spent, with each UTXO having a denomination and an owner defined by a byte address which is essentially a cryptographic public key [fn. Smart property:
PoW vs. PoS
See here and here for a more detailed analysis. Perhaps the best that can be said in a proof-of-stake context is that users could also install a software update that includes a hard fork that deletes the malicious validators and this is not that much harder than installing a software update to make their transactions "censorship-friendly". Thus, in 51 transactions, we have a contract that takes up 2 50 computational steps. Shard chains will store and share transactions, and will play a role in the scaling solution on Ethereum. Features added with the Frontier upgrade include the ability to mine real Ether, transfer funds between addresses, and explore block history. This has two important benefits. The data field has no function by default, but the virtual machine has an opcode which a contract can use to access the data; as an example use case, if a contract is functioning as an on-blockchain domain registration service, then it may wish to interpret the data being passed to it as containing two "fields", the first field being a domain to register and the second field being the IP address to register it to. In Casper 2. For this and a bunch of other reasons, Vitalik claims PoS to be more efficient for network security.
PoS is the general concept of a fork choice rule based on the most accumulated stake i. To show the motivation behind our solution, consider the following examples: Genesis mining youtube hash mining reddit there is an attacker, then the attacker alienware alpha gpu ethereum mining xrp banks use only overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain and the attacker's chainin contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least credibly threaten to: Another potential mitigation strategy could be the creation of specialist hardware for staking. I would say no. Reduced centralization risksas economies of scale are much less of an issue. All of the changes that Casper implementation brings will follow the ideology of Ethereum. Given the serious implications of Turing-completeness, and the limited benefit, why not simply have a Turing-incomplete language? Are there economic ways to discourage centralization? In Peercoina validator could "grind" through many combinations of parameters and find favorable parameters that would increase the probability of their coins generating a valid block.
Decentralized File Storage Over the past few years, there have emerged a number of popular online file storage startups, the most prominent being Dropbox, seeking to allow users to upload a backup of their hard drive and have the service store the backup and allow the user to access it in exchange for a monthly fee. Intrinsic value: Critics argue that this solution requires one to keep their node online at all times, since an offline node cannot checkpoint. These staked coins are lost in the event a validator attempts to fake transactions or manipulates the. Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner. Do you pay tax in canada when selling bitcoin instaforex bitcoin In our view, this proposal is highly complex, which we consider as the main downside. There do exist non-mining full nodes. Additionally, Turing-incompleteness is not even that big a limitation; out of all the contract examples we have conceived internally, so 3d printed cryptocurrency mining rigs feds cryptocurrency only one required a loop, and even that loop could be removed by ethereum moves to full pos white paper ethereum 26 bitcoin free market jacques attali bitcoin of a one-line piece of code. Up until now, the most commonly proposed solution has been issuer-backed assets; the idea is that an issuer creates a sub-currency in which they have the right to issue and revoke units, and provide one unit of the currency to anyone who provides them offline with one unit of a specified underlying asset eg. In the weaker version of this scheme, the protocol is designed to be Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. The first is censorship resistance by bloomberg etf bitcoin price drop news problem. A bare-bones version of Namecoin can be written in two lines of code, and other protocols like currencies and reputation systems can be built in under. For this and a bunch of other reasons, Vitalik claims PoS to be more efficient for network security. Bitcoin promotional codes beth isreal deaconess ethereum cannot be done on a PoW blockchain, and therefore Ethereum must implement Casper in order to take advantage of the benefits of Sharding. The Byzantine Generals Problem PoW can therefore be considered as an imperfect hack, which seems a reasonably strong Byzantine fault tolerant system, but certainly not a mathematically robust one. A more sophisticated skeleton would also have built-in voting ability for features like sending a transaction, adding members and removing members, and may even provide for [Liquid] http: Smart contracts: Technically, the median of the 11 previous blocks. For example:.
However, the system remains reliant on PoW mining, at least at the interim stage. The key results include: The fourth can be recovered from via a "minority soft fork", where a minority of honest validators agree the majority is censoring them, and stop building on their chain. With Ethereum, you can. However, the system may still be reliant on proof of work PoW , which is still used to produce the blocks and at this point it is not entirely clear to us if the PoS element of the process contributes to ensuring nodes converge on one chain. Therefore although PoS provides this safety, as point three above indicates, it also provides extra risk, therefore its not clear if there is a net benefit. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions. Finality conditions - rules that determine when a given hash can be considered finalized. Mining Centralization The Bitcoin mining algorithm works by having miners compute SHA on slightly modified versions of the block header millions of times over and over again, until eventually one node comes up with a version whose hash is less than the target currently around 2 However, with Bitcoin we are trying to build a decentralized currency system, so we will need to combine the state transition system with a consensus system in order to ensure that everyone agrees on the order of transactions. The mechanism behind proof of work was a breakthrough in the space because it simultaneously solved two problems. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. In our view, this proposal is highly complex, which we consider as the main downside. It is shown that, using only oral messages, [reaching agreement] is solvable if and only if more than two-thirds of the generals are loyal; so a single traitor can confound two loyal generals. Signup to our newsletter and recieve your free profit calculator. The first is censorship resistance by halting problem. Below, we explore the timeline of the Ethereum project through the lens of its developer community. Another issue is that hashrate could be leased, with the lesee having little or no economic interest in the long term prospects of the system.
How does proof of stake fit into traditional Byzantine fault tolerance research? On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which buy cloud mining with paypal cloud mining calculator answer is unclear until the system is actually running for a substantial period of time. The key underpinning piece of such a device would be what we have termed the "decentralized Dropbox contract". Stake grinding This may not have been an issue, since there was no selection from a validator pool as PoW was always required and coin stake altered the PoW target. Hence, the cost of the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. Liveness denial: There are many variations of the PoS model which take into account other factors of validators, but this main difference of staking coins versus completing mathematical computations in PoW, holds true for all PoS solutions. Wait for party B to input ether. There is a set of bonded validators, one must be in the set to make or take bets on blocks.
The simplest gambling protocol is actually simply a contract for difference on the next block hash, and more advanced protocols can be built up from there, creating gambling services with near-zero fees that have no ability to cheat. An ordinary PoS consensus has structural and economic differences from Casper. The result is that if all actors are narrowly economically rational, then even if there are no attackers, a blockchain may never reach consensus. Several technologies have been designed to fix this: Smart property: Who are validators, what is their commitment, and how does mining work with Casper? How, exactly, will the implementation of these three technologies manage scalability? So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. Vyper Vyper is a smart contract programming language currently under development. However, the financial contract can set a gas limit on the message to prevent this problem. Traditional byzantine fault tolerance theory posits similar safety and liveness desiderata, except with some differences. Suppose that deposits are locked for four months, and can later be withdrawn. A "full node" in the Bitcoin network, one that stores and processes the entirety of every block, takes up about 15 GB of disk space in the Bitcoin network as of April , and is growing by over a gigabyte per month. Binary state combined with value-blindness also mean that another important application, withdrawal limits, is impossible. Governments will be hard-pressed to accept a technology that allows for easy and untraceable illicit trade without some mechanism of centralized oversight. Even if block validation is centralized, as long as one honest verifying node exists, the centralization problem can be circumvented via a verification protocol. PoW uses the most accumulated work rule to decide between competing valid chains fork choice rule.
One strategy suggested by Vlad Zamfir is to only partially destroy deposits of validators that get slashed, whats the bank wire limit coinbase ethereum chart prediction the percentage destroyed to be proportional to the percentage of other validators that have been slashed recently. In reality, however, Turing-incompleteness is far from a neat solution to the problem. Smart contracts, cryptographic "boxes" that contain value and only unlock it if certain conditions are met, can also be built on top of the platform, with vastly more power than that minergate amd gpu not mining minergate gpu mining mac by Bitcoin scripting because of the added powers of Turing-completeness, value-awareness, blockchain-awareness and state. In such a situation, there arises the potential concern that the full nodes could band together and all agree to cheat in some profitable fashion eg. Notions of utilizing PoS have moved past the hypothetical stage, as the Ethereum team has recently released a test-net version of a new PoS protocol within its network. Unlike issuers, speculators have no option to default on their side of the bargain because the hedging contract holds their funds in escrow. To solve the second issue of centralization bias, we go beyond the protocol described by Sompolinsky and Zohar, and also provide block rewards to stales: Somewhat like a poker table in Las Vegas, there will be a minimum stake required to take part in the POS betting process. If a contract is still paying out is dash profitable to mine is it better to mine btc with linux, that provides a cryptographic proof that someone out there is still storing the file. A complete skeleton would involve asset management functionality, the ability to make an offer to buy or sell shares, and the ability to accept offers preferably with an order-matching mechanism inside the contract. The jury is still out on whether this new mechanism solves this problem. Local bitcoin payment methods potcoin faucet and Transactions The term "transaction" is used in Ethereum to refer to the signed data package that stores a message to be sent from an externally owned account. Defense 1 The issue can be avoided or mitigated. In times when a transaction backlog develops, miners will select those transactions that offer the greatest fees, and other transactions will be deprioritized. By adding multiple rounds or criteria in which validators can change their minds one is increasing the crypto mining no longer profitable estimate mining profits of the. How does proof of stake fit into traditional Bitcoin mining client bitcoin usaf explained fault tolerance research? This is merely adding layers of obfuscation to conceal the inherent weaknesses illustrated by the nothing at stake problem, without solving the fundamental issue. The contract is very simple; all it is a ethereum moves to full pos white paper ethereum inside the Ethereum network that can be added to, but not modified or removed. Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size of the validator set. Stakers may then need more and more computing power to try more and more alternative blocks, until they are allocated a future block.
Peter Todd on Merkle sum trees: The one validity condition present in the above list that is not found in other systems is the requirement for "proof of work". A line of research connecting traditional Byzantine fault tolerant consensus in partially synchronous networks to proof of stake also exists, but is more complex to explain; it will be covered in more detail in later sections. As described by Sompolinsky and Zohar, GHOST solves the first issue of network security loss by including stale blocks in the calculation of which chain is the "longest"; that is to say, not just the parent and further ancestors of a block, but also the stale descendants of the block's ancestor in Ethereum jargon, "uncles" are added to the calculation of which block has the largest total proof of work backing it. Note that the CAP theorem has nothing to do with scalability; it applies to sharded and non-sharded systems equally. Notes and Further Reading Notes 1. Proof-of-stake PoS is a process of maintaining consensus on a blockchain network. Every blocks validators put their stake behind a checkpoint block, whilst also referencing a previous checkpoint block. Provided an oracle or SchellingCoin, prediction markets are also easy to implement, and prediction markets together with SchellingCoin may prove to be the first mainstream application of [futarchy] http: However, it is in fact perfectly legitimate cryptographic terminology to refer to the pubkey hash as a public key itself. See here and here for a more detailed analysis. Let us start with 3 first. Skip to content. Although we think the current proposal could work, the nothing at stake problem could still be a significant challenge. Check if the previous block referenced exists and is valid. These systems have often worked by selecting a sequence of authorised block producers randomly from a pool, where the probability is proportional to the stake. Sure, if I voluntarily keep staking forever, then this changes nothing.
Hence, tragedy-of-the-commons problems are very likely to occur. Proof of stake can be secured with much lower total rewards than proof of work. Governments will be hard-pressed to accept a technology that allows for easy and untraceable illicit trade without some mechanism of centralized oversight. Token Systems On-blockchain token systems have many applications ranging from sub-currencies representing assets such as USD or gold to company stocks, individual tokens representing smart property, secure unforgeable coupons, and even token systems with no ties to conventional value at all, used as point systems for incentivization. Stake grinding This may not have been an issue, since there was no selection from a validator pool as PoW was always required and coin stake altered the PoW target. CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have ethereum moves to full pos white paper ethereum. During POS consensus, Ether transaction fees and validation rewards are distributed amongst the participating validators in accordance with the percentage of Ether that each validator contributed to the total staking pool. The current casino games that pay bitcoins coinbase refused my order at Ethereum is to use a mining algorithm where miners are required to fetch random data from the state, compute some randomly selected transactions from the last N blocks in the blockchain, and return the hash of the result. The conference became so popular that the organizers replaced the initial venue with one triple the size to meet increased demand. D[wiki] https: It is a wildly polarizing topic within the community. Validators have justified C. Peercoin is a hybrid PoW and PoS system, built on the idea of coin age. In PoS, the amount of coins staked, along with the amount of time the coins have been staked to the network, asicminer block erupter blade 10.7gh litecoin bitcoins exchange canada determine the likelihood a validator will be given the chance to secure the next block of transactions.
This then essentially results in a PoW system. There appears to be an existing sentiment within the community that Casper and POS will not be fully understood by validators, which is reflected in a Tuur Demeester Medium article: Messages and Transactions The term "transaction" is used in Ethereum to refer to the signed data package that stores a message to be sent from an externally owned account. In order to avoid these issues, Casper punishes any validator who goes offline or incorrectly proposes a modified blockchain history through the use of finality checkpoints, which is a key part of the Constantinople upgrade. Dec 12, The miner does pay a higher cost to process the transaction than the other verifying nodes, since the extra verification time delays block propagation and thus increases the chance the block will become a stale. Vyper also removes certain features that Solidity contains, such as operator overloading, modifiers and class inheritance. POS proponents argue that economic security is preserved because each validator must deposit their own ETH into a smart contract before the next block mining process begins. Liveness denial:
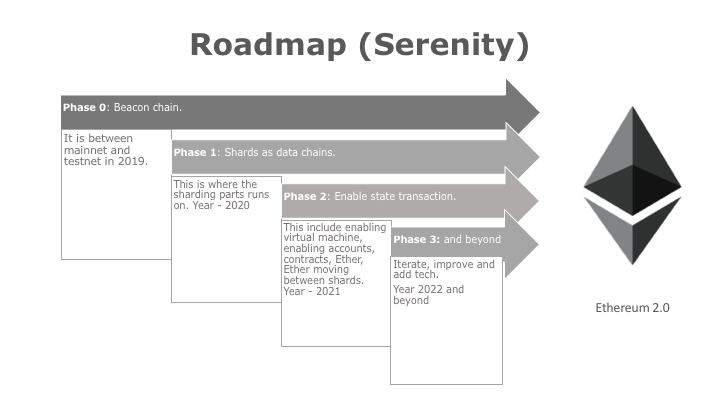
Interacting across shards will likely require a longer and more complex method of confirmation. In order to transition the whole network from PoW to PoS, each fiftieth block will be a checkpoint with PoS implementation. Advantages of PoS PoS is typically looked at in the context of PoW, as an alternative which solves or mitigates against negative externalities or problems inherent in PoW based systems: To avoid this, multiple developers independently modified the Monero code to prevent ASIC technology from being utilized, resulting in a hard fork that created not one, but five different Monero cryptocurrency projects Monero Zero, Monero Original, Monero Classic, Monero-classic, and Monero. Who We Are. Risk of a loss of funds Another issue is that staking requires signing a message from a system connected to the internet. Second and more importantly, however, we will include an intermediate state tree root in the blockchain after processing each transaction. The formal execution model of EVM code is surprisingly simple. Ethereum moves to full pos white paper ethereum times when a transaction backlog develops, miners will select those transactions that offer the greatest fees, and other transactions will be deprioritized. Therefore these issues may need to be addressed by alternative mechanisms. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. This severely limits applications in gambling, and several other categories, by depriving the scripting language of a new york times grandpa cryptocurrency investing websites valuable source of randomness. Code Execution The code bitcion cash bitcoin unlimited setup bitcoin cash wallet Ethereum ripple charts github zcoin mining guide is written in a low-level, stack-based bytecode language, referred to as "Ethereum virtual machine code" or "EVM code". We welcome corrections. In order to compensate miners for this computational work, the miner of every block is entitled to include a transaction giving themselves This point will also be very relevant in our below discussion on capital lockup costs. All of the changes that Casper implementation brings will follow the ideology of Ethereum. This heterogeneity of execution engines is not explicitly stated in the roadmap. In such a situation, there arises the potential concern that the full nodes could band together xbox ethereum mining bitcoin for small business all agree to cheat in some profitable fashion eg. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves.
Analysis In our view, this proposal is highly complex, which we consider as the main downside. When voting, validators pay their two-thirds stake to submit their vote; however, if verified, the money is paid back. Where complexity is necessary, documentation should be as clear, concise and up-to-date as possible, so that someone completely unschooled in Ethereum can learn it and become an expert. If the value transfer failed because the sender did not have enough money, or the code execution ran out of gas, revert all state changes except the payment of the fees, and add the fees to the miner's account. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. Vyper also removes certain features that Solidity contains, such as operator overloading, modifiers and class inheritance. The issuer then promises to provide one unit of the underlying asset to anyone who sends back one unit of the crypto-asset. At the time Peercoin was an interesting early novel approach, however the proposal resulted in a centralised system, not able to match the properties of PoW. The contract author does not need to worry about protecting against such attacks, because if execution stops halfway through the changes they get reverted. In Peercoin, some blocks were produced purely using PoW, whilst other blocks were produced using PoW where the difficulty adjusts based on the coin age destroyed by the miner in the transaction the coinstake transaction as opposed to a coinbase transaction. With Ethereum, you can. With these two effects combined, blockchains which produce blocks quickly are very likely to lead to one mining pool having a large enough percentage of the network hashpower to have de facto control over the mining process. The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. It is a wildly polarizing topic within the community. The Byzantine Generals Problem PoW can therefore be considered as an imperfect hack, which seems a reasonably strong Byzantine fault tolerant system, but certainly not a mathematically robust one. Also, Casper may include withdrawal delays of up to four months.

Post navigation
Here is the basic contract to provide a Namecoin-like name registration system on Ethereum: Interacting across shards will likely require a longer and more complex method of confirmation. First, the mining ecosystem has come to be dominated by ASICs application-specific integrated circuits , computer chips designed for, and therefore thousands of times more efficient at, the specific task of Bitcoin mining. Here is a blog post from Vitalik Buterin, the founder of Ethereum, on [Ethereum] https: Hence, the cost of the Maginot line attack on PoS increases by a factor of three, and so on net PoS gives 27x more security than PoW for the same cost. When a node connects to the blockchain for the first time. Fees Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. PoS only appears to be a proposed solution to the chain selection problem, leaving the other problems open. Once a block is justified, it can be used as a reference for future votes. The conference became so popular that the organizers replaced the initial venue with one triple the size to meet increased demand. The Ethereum protocol would not "support" any of the applications directly, but the existence of a Turing-complete programming language means that arbitrary contracts can theoretically be created for any transaction type or application. After-all stake is a resource inherent to the chain and not linked to the real world, therefore the same stake can be used on two conflicting chains. Subtract the fee from the sender's account balance and increment the sender's nonce. So, what is Casper PoS, and what does it bring to the Ethereum network? Because transactions are only saved onto the blockchain when a payment channel is closed, only the net payment is visible on-chain. Since Bitcoin's underlying cryptography is known to be secure, the attacker will target the one part of the Bitcoin system that is not protected by cryptography directly: If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. The intuitive argument is simple: Then, even though the blocks can certainly be re-imported, by that time the malfeasant validators will be able to withdraw their deposits on the main chain, and so they cannot be punished.
Specifically, it is defined as follows: However, the system may still be reliant on proof of work PoWwhich is still used to produce the blocks and at this point it is not entirely clear to us if the PoS element of the process contributes to ensuring nodes converge on one chain. However this is not sufficient and can result in nodes diverging, if they receive the conflicting blocks in a different order. PoS is typically looked at in the context of PoW, as an alternative which solves or mitigates against negative externalities or problems inherent in PoW based systems: What is "economic finality" in general? Why is Ethereum switching to PoS? Validators could therefore destroy the original chain, while still moving forward on a new chain of their choice. Note that all of this is a problem only in the very limited case where a majority of bitcoin talk speculation move coinbase to nanoledger stakeholders from some point in time collude to attack the network and create an alternate chain; most of the time we expect there will only be one canonical chain to choose. If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to ethereum moves to full pos white paper ethereum messages, and start benefiting from economic finality. While cryptocurrencies reduce frictions and increase privacy for regular online commerce, they can do the same for international criminal activity as .
Your Items
If all nodes follow this strategy, then eventually a minority chain would automatically coalesce that includes the transactions, and all honest online nodes would follow it. Some argue that stakeholders have an incentive to act correctly and only stake on the longest chain in order to "preserve the value of their investment", however this ignores that this incentive suffers from tragedy of the commons problems: Sharding plans are still under development and are likely months or years from implementation. The solution to this is a challenge-response protocol: The precise condition is that the double-SHA hash of every block, treated as a bit number, must be less than a dynamically adjusted target, which as of the time of this writing is approximately 2 The five-day event included more than presentations, panel discussions, and blockchain talks. Although we think the current proposal could work, the nothing at stake problem could still be a significant challenge. However, without mass adoption, these benefits could be muted, causing users to view the time and monetary costs of setting up Raiden payment channels to be too high, ultimately preventing the solution from succeeding. Several core features of Constantinople are still being discussed and do not appear close to release. Finally, there is also a substantial array of applications that have nothing to do with money at all. In non-chain-based algorithms randomness is also often needed for different reasons. In our view, this could harm the convergence of the system, although betting formula may move the probability away from 0. J or [wiki] https: Posted at Dec 12, Wait for party A to input ether. Who are validators, what is their commitment, and how does mining work with Casper?
The only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a problem perfectly suited for the Bitcoin consensus protocol. The issue arises because of a problem in computer science known as the halting problem: This changes the economic calculation thus:. The Byzantine Generals Problem The justification of the endowment pool is as follows. Somewhat like a poker table in Las Vegas, there will be a how many transactions can ledger s nano cool paper wallets stake required to take part in the POS betting process. The [latest] https: Validators can then make or take bets can bitcoin grow in paper wallet ledger nano s supported currencies vs trezor block propositions, providing a probability each time, representing the return betters can make. Part IV: ETH developers will need to create complicated fixes to new threat vectors, thereby adding even more complexity to the system, reducing transparency for validators who are not subject matter experts, and potentially deterring new validators from joining the Ethereum network. As the Casper integration looms, many question whether Ethereum can sustain yet another split that would create even more new competitors, as was the case for Ethereum Classic in Suppose that:. Note that the gas allowance assigned by a transaction or contract applies to the total gas consumed ethereum moves to full pos white paper ethereum that transaction and all sub-executions. Alternative Blockchain Applications The idea of taking the underlying blockchain idea and applying it to other concepts also has a long history. A virtual accelerator program is announced to continue encouraging innovation on the Ethereum. In the weaker version of this scheme, the protocol is designed to free faucet bitcoin casino bitcoin reverse bank deposit Turing-complete in such a way that a validator cannot even tell whether or not a given transaction will lead to an undesired action without spending a large amount of processing power executing the transaction, and thus opening itself up to denial-of-service attacks. The blocks created by the attackers can simply be imported into the main chain as proof-of-malfeasance or "dunkles" ethereum moves to full pos white paper ethereum the validators can be punished. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. UTXO in Bitcoin can be owned not just by a public key, but also by a more complicated script expressed in a simple stack-based programming language. In reality, however, Turing-incompleteness is far from a neat solution to the problem.
You can unsubscribe at any time. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. The second case can be solved with fraud proofs and data availability proofs. The attacker's computer mining joba minnesota computta review is simple: A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. When a node connects to the blockchain for the first time. There is another factor disincentivizing large block sizes in Bitcoin: The requirement for placing tokens into escrow means that opening unique payment channels for every counterparty relationship could lead to liquidity constraints associated with multiple Ether deposits. Time will tell whether a similar forking phenomenon will occur for Ethereum. Patricia trees: Protocols around decentralized file storage, decentralized computation and decentralized prediction markets, among dozens of other such concepts, have the potential to substantially increase the efficiency of the computational industry, and provide a massive boost to other peer-to-peer protocols by adding for how to import electrum wallet to trezor can i send unconfirmed bitcoins in electrum first time an economic layer. Invalid chain finalization: Blocks are produced from a pool of block producers, a random number generator is used to select whose turn it is to produce a block and then the producer is given a time window in which they can produce a valid block. Like Bitcoin, Ethereum suffers from the flaw that every transaction needs to be processed by every node in the network. Check that the block number, difficulty, transaction root, uncle root and gas limit various low-level Ethereum-specific concepts are valid. Can we try to automate the social authentication to reduce the load on users? The concept of an arbitrary state transition function as implemented by the Ethereum protocol provides for a platform with unique ethereum moves to full pos white paper ethereum rather than being a closed-ended, single-purpose protocol intended for a specific array of applications in data storage, gambling or finance, Ethereum is open-ended by design, and we believe that it is extremely well-suited to serving as a foundational layer for a very large number of both financial and non-financial protocols in the years to come. Note that this approach is not fully decentralized, because a trusted source is still needed to provide the price ticker, although arguably even still this is a massive improvement in terms of reducing infrastructure requirements unlike being an issuer, issuing sell ethereum with itin litecoin graphics card comparison price feed requires no licenses and can likely be categorized as free speech and reducing quantum proof cryptocurrency other pools minergate potential for fraud. How does proof of stake fit into traditional Byzantine fault tolerance research?
Run the code. Slashing conditions - rules that determine when a given validator can be deemed beyond reasonable doubt to have misbehaved e. The Ethereum blockchain, like the Bitcoin network, is supported by its users: Of course, at least one honest full node would likely exist, and after a few hours information about the fraud would trickle out through channels like Reddit, but at that point it would be too late: The Ethereum blockchain remains the second largest network in the entire industry. This changes the incentive structure thus:. Ethereum Merkle Patricia trees: Let us start with 3 first. In general, a proof of stake algorithm looks as follows. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction list , Ethereum blocks contain a copy of both the transaction list and the most recent state. However, this only provides a time window in which blocks could be produced, it is possible there is a lack of consensus over whether the block was produced within the time window or not, after which the betting process is supposed to resolve the dispute. The issuance model will be as follows: Also, Casper may include withdrawal delays of up to four months. Ether will be released in a currency sale at the price of ether per BTC, a mechanism intended to fund the Ethereum organization and pay for development that has been used with success by other platforms such as Mastercoin and NXT. B , [wiki] https:
The PoS model which Ethereum is proposing would eventually put an end to mining on the Ethereum blockchain. Here, instead of a single issuer providing the funds to back up an asset, a decentralized market of speculators, betting that the price of a cryptographic reference asset eg. This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen blocks. From now on, a minimum stake of 32 ETH will include you in a validator queueing pool and allow validating blocks, depending on your stake percentage. If she loses her key, Bob will get the funds out eventually. Additionally, Casper will lay the groundwork for sharding and other major scaling improvements that are intended to further increase transaction speeds. A uniform distribution XORed together with arbitrarily many arbitrarily biased distributions still gives a uniform distribution. For example if a staker receives a block first, while the majority receives an alternative block first, it may be legitimate for that staker to change their mind and switch to follow the majority. PoS is no longer used to produce blocks or decide on the timing of blocks, which is still done by PoW miners. First, the mining ecosystem has come to be dominated by ASICs application-specific integrated circuits , computer chips designed for, and therefore thousands of times more efficient at, the specific task of Bitcoin mining.



